Set up the Certificate Authority Server (Public Key Infrastructure)
This is the third post of The Complete Guide to Hyperledger Fabric in 2023.
The first post includes 5 steps to Set up the Blockchain Network.
Step 1: Open Docker Desktop, to let the Docker Daemon runs
Step 2: Clone the Hyperledger Fabric Sample repository, pull down the Docker images, and download the platform-specific binary
Step 3: Add the bin sub-directory into the PATH environment variable
Step 4: Bring up the network
Step 5: Create a channel
The second post includes 6 steps to Deploy, invoke the Chaincode (Smart Contract), and Interact with the Network.
Step 6: Stream logs to the terminal with Logspout
Step 7: Package the smart contract into chaincode
Step 8: Install the chaincode onto the peer(s)
Step 9: Approve the chaincode definition as peer
Step 10: Commit the chaincode defintion to channel
Step 11: Invoke the chaincode
Therefore, don't move on to Step 12 until you finished the setup with first and second post.
1st post: Set up the Blockchain Network
2nd post: Deploy, invoke the Chaincode (Smart Contract), and Interact with the Network
Step 12: Download the CA-server and CA-client binaries
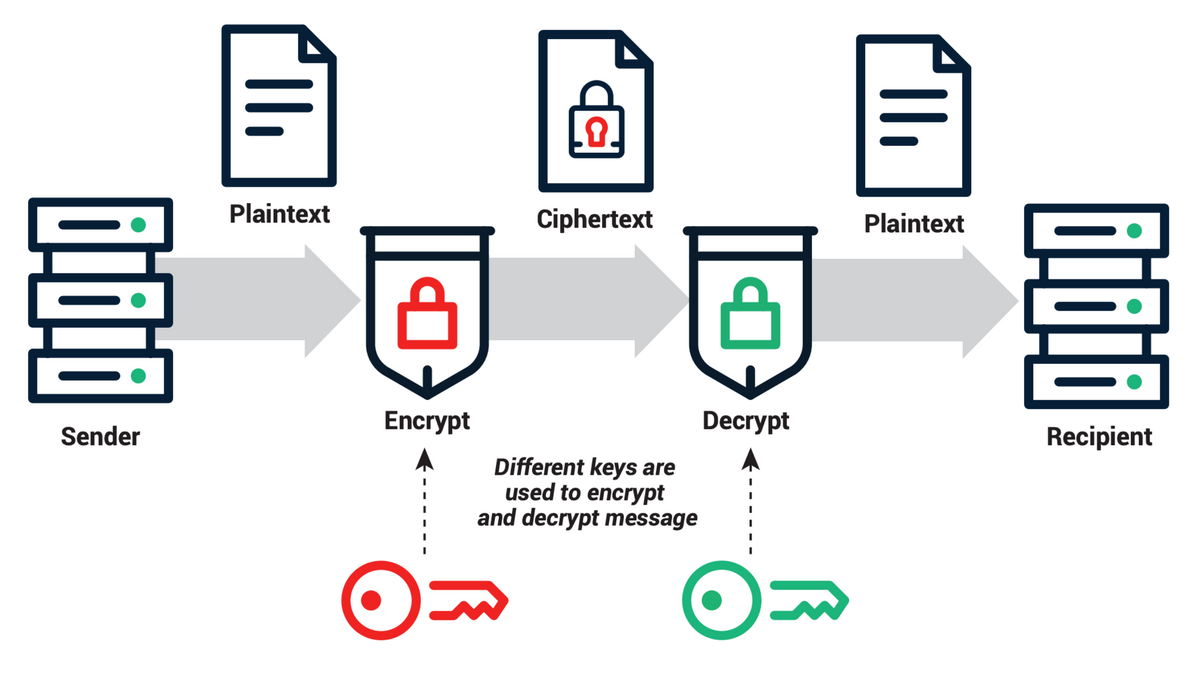
CA stands for Certificate Authority. It comprises of: CA-server, and CA-client. It's a core component in the Hyperledger Fabric blockchain network. Throughout this tutorial, I'll use CA the handy form, instead of Certificate Authority, to illustrate the development process.
Let's head over to the Fabrc-CA GitHub here. And scroll down to the Assets drop-down list. Choose the zip file that matches your machine type. Download it to a clean directory on your machine.
You will see a bin folder that contains the binaries after you upzip the file.
Step 13: Initialize the TLS-CA-server
At the 2nd post, from Step 7 onwards, you're operating from the {Your fabric-samples repo}/test-network directory. Before you create a TLS-CA-server, you have to set up its own directory at the root level. Let's go up one level:
cd ..
And create the folder:
mkdir fabric-ca-server-tls
The reason to append -tls to the folder name fabric-ca-server while you're constructing the base directory for the TLS-CA-Server is: the TLS-CA-server will facilitate the TLS communication in the production environment.
Next up, copy the fabric-ca-server binary and paste into this folder.
And go into the newly created directory:
cd fabric-ca-server-tls
Then execute the binary to initialize the server by specifying the admin user id and password. tls-admin and tls-adminpw are just made up. You can use whatever user id and password you want:
fabric-ca-server init -b tls-admin:tls-adminpw
A TLS-CA-server admin is just created. More details:
Terminal (TLS-CA-server)
2023/03/17 16:43:21 [INFO] Created default configuration file at /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-server-tls/fabric-ca-server-config.yaml
2023/03/17 16:43:21 [INFO] Server Version: 1.5.5
2023/03/17 16:43:21 [INFO] Server Levels: &{Identity:2 Affiliation:1 Certificate:1 Credential:1 RAInfo:1 Nonce:1}
2023/03/17 16:43:21 [WARNING] &{69 The specified CA certificate file /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-server-tls/ca-cert.pem does not exist}
2023/03/17 16:43:21 [INFO] generating key: &{A:ecdsa S:256}
2023/03/17 16:43:21 [INFO] encoded CSR
2023/03/17 16:43:21 [INFO] signed certificate with serial number 188715849213452429727584608538328033511894701871
2023/03/17 16:43:21 [INFO] The CA key and certificate were generated for CA
2023/03/17 16:43:21 [INFO] The key was stored by BCCSP provider 'SW'
2023/03/17 16:43:21 [INFO] The certificate is at: /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-server-tls/ca-cert.pem
2023/03/17 16:43:21 [INFO] Initialized sqlite3 database at /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-server-tls/fabric-ca-server.db
2023/03/17 16:43:21 [INFO] The issuer key was successfully stored. The public key is at: /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-server-tls/IssuerPublicKey, secret key is at: /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-server-tls/msp/keystore/IssuerSecretKey
2023/03/17 16:43:21 [INFO] Idemix issuer revocation public and secret keys were generated for CA ''
2023/03/17 16:43:21 [INFO] The revocation key was successfully stored. The public key is at: /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-server-tls/IssuerRevocationPublicKey, private key is at: /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-server-tls/msp/keystore/IssuerRevocationPrivateKey
2023/03/17 16:43:21 [INFO] Home directory for default CA: /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-server-tls
2023/03/17 16:43:21 [INFO] Initialization was successful
And a bunch of artifacts are created alongside the fabric-ca-server binary:

Step 14: Modify the TLS-CA-server configuration
Now that you have initialized your server, you can edit the generated fabric-ca-server-config.yaml file to modify the default configuration settings. At a bare minimum, you need to configure 6 parameters to get it up and running. Let's go through it one by one.
First two of all are port related:port and operations.listenAddress. In the fabric-ca-server-config.yaml file, they're located at:
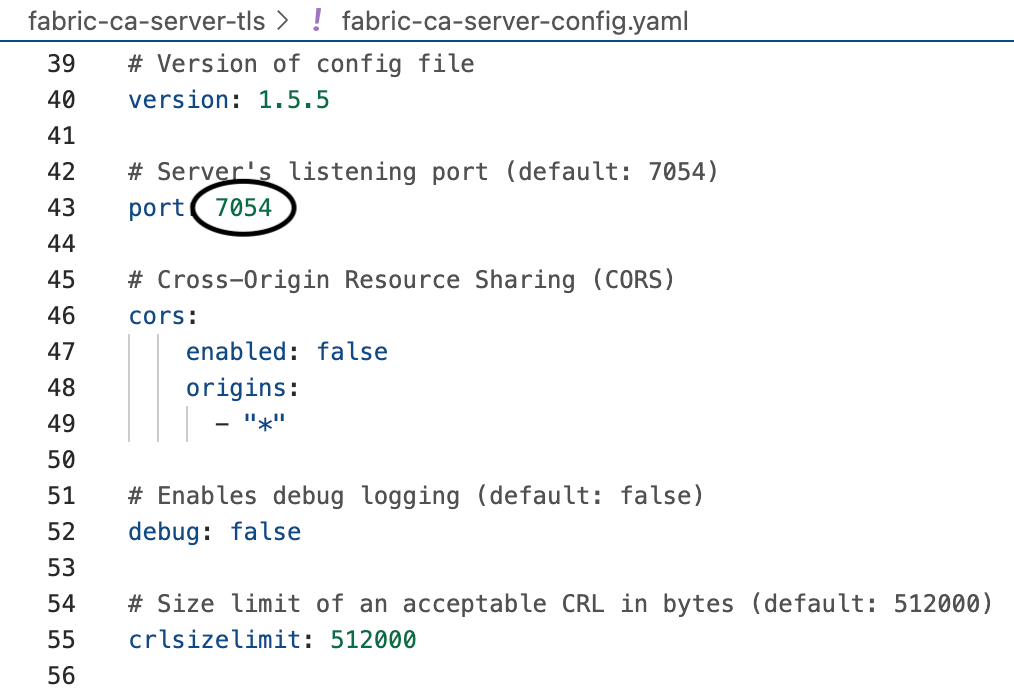
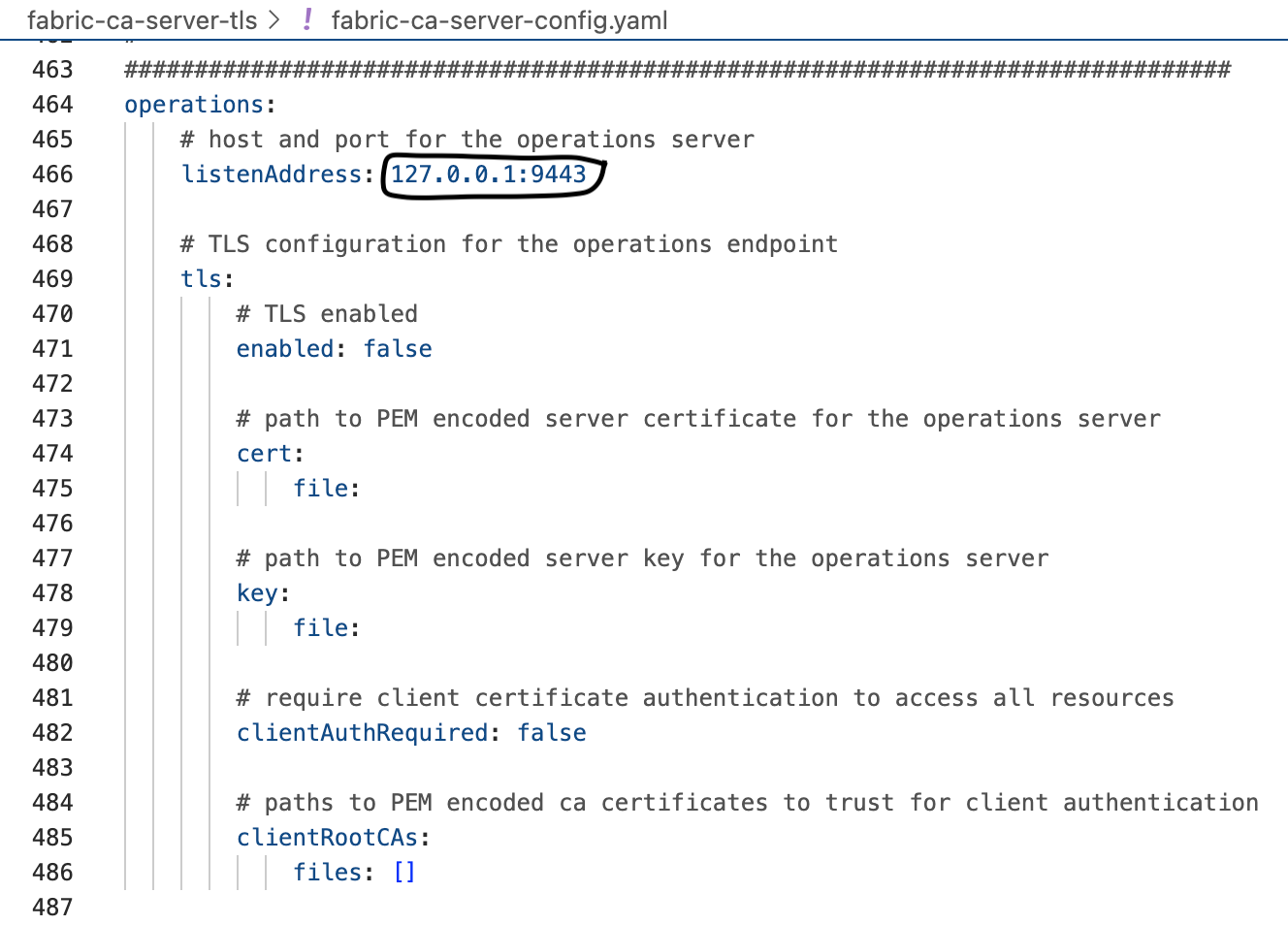
You need to ensure these two parameters are set to use the ports that are free-to-use. To check against them, run:
lsof -i -n -P | grep TCP
It will show something like:
Terminal (TLS-CA-server)
Google 1055 aerobot 69u IPv4 0x5e8c650525083127 0t0 TCP 10.0.1.5:49284->104.18.70.113:443 (ESTABLISHED)
Google 1055 aerobot 72u IPv4 0x5e8c650525084767 0t0 TCP 10.0.1.5:49286->54.77.128.32:443 (ESTABLISHED)
Code\x20H 1765 aerobot 20u IPv4 0x5e8c65052508d287 0t0 TCP 10.0.1.5:49250->13.107.5.93:443 (ESTABLISHED)
Code\x20H 1765 aerobot 22u IPv4 0x5e8c650525096e67 0t0 TCP 10.0.1.5:49255->13.107.42.18:443 (ESTABLISHED)
Code\x20H 1765 aerobot 23u IPv4 0x5e8c650525087987 0t0 TCP 10.0.1.5:49251->117.18.232.200:443 (ESTABLISHED)
As long as your machine is not using the ports you intend to use for these two parameters, you're set.
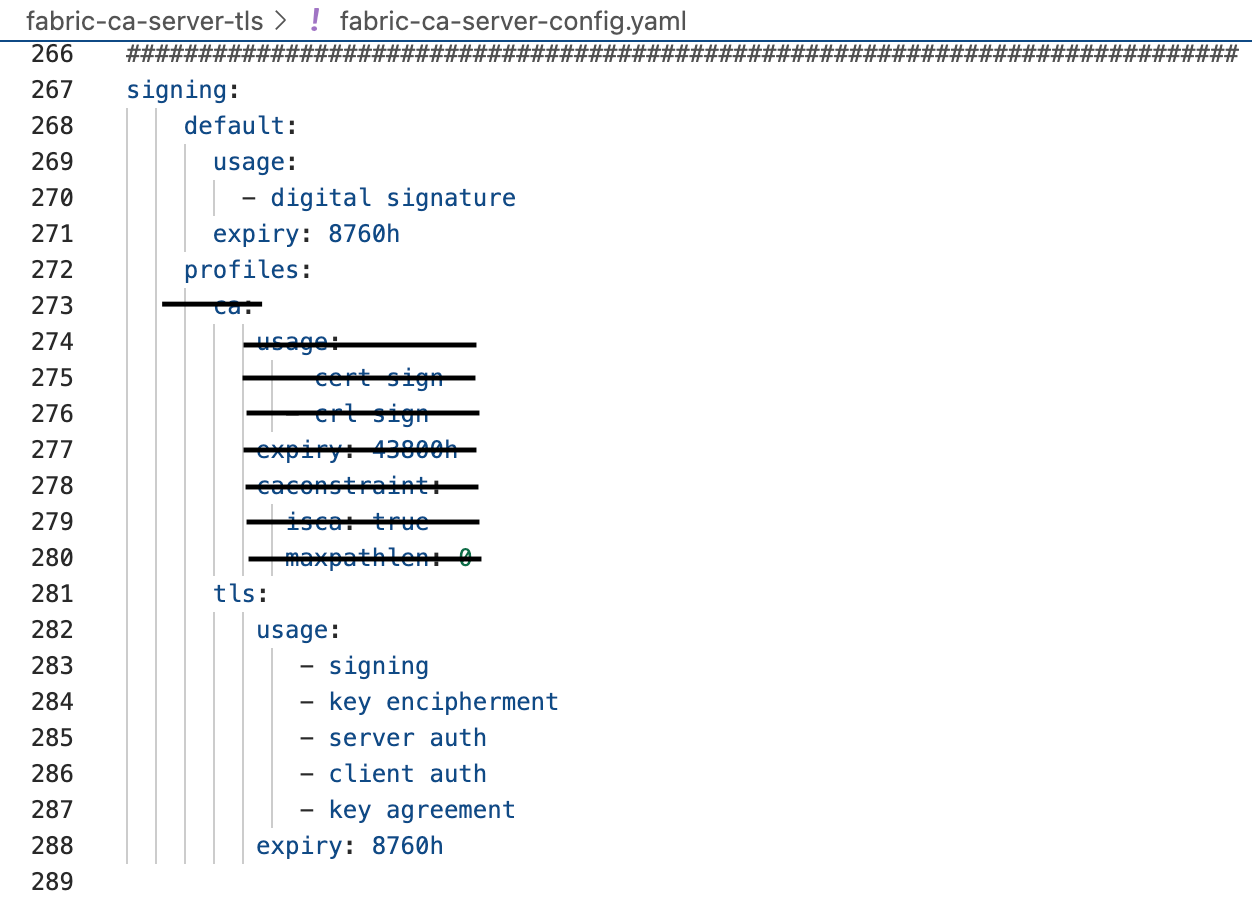
The 3rd one is tls.enabled. By default, it is disabled.
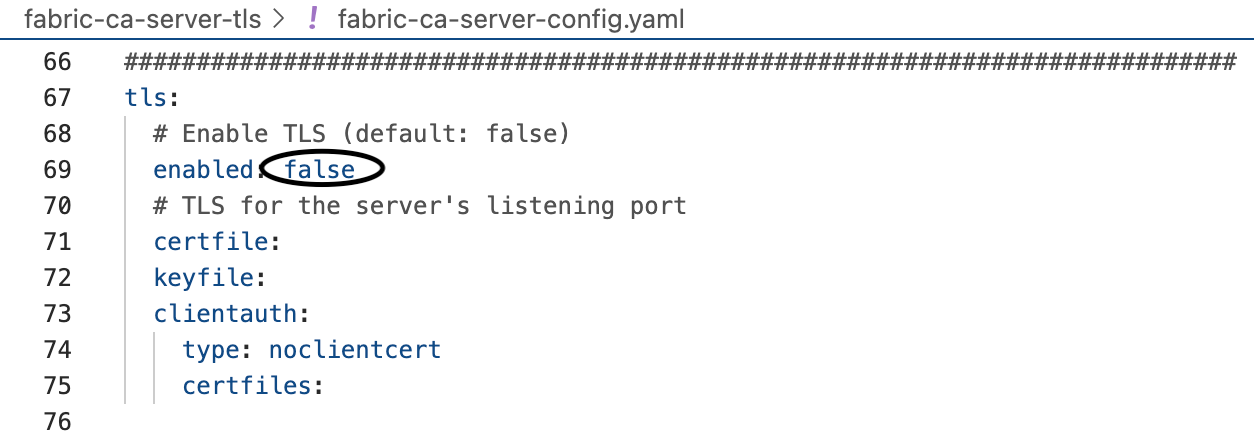
Set this value to true. So, when you start the server in the next step, a TLS signed certificate tls-cert.pem file will be generated. This is the certificate the server will present to the client during a TLS handshake.
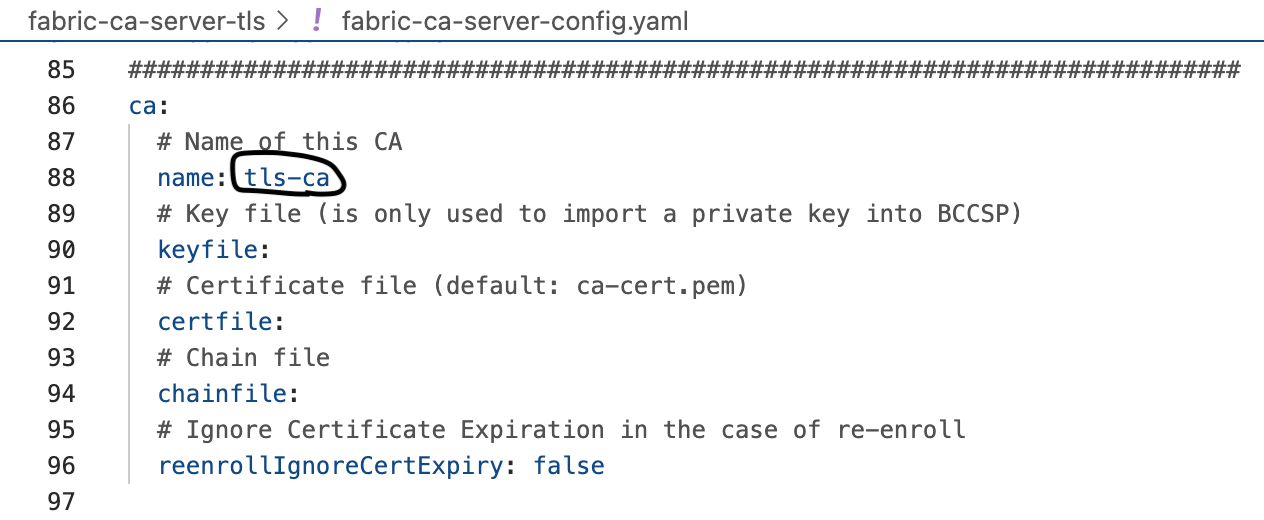
The 4th one is ca.name. Use whatever name you want, or go semantic, for example: tls-ca.
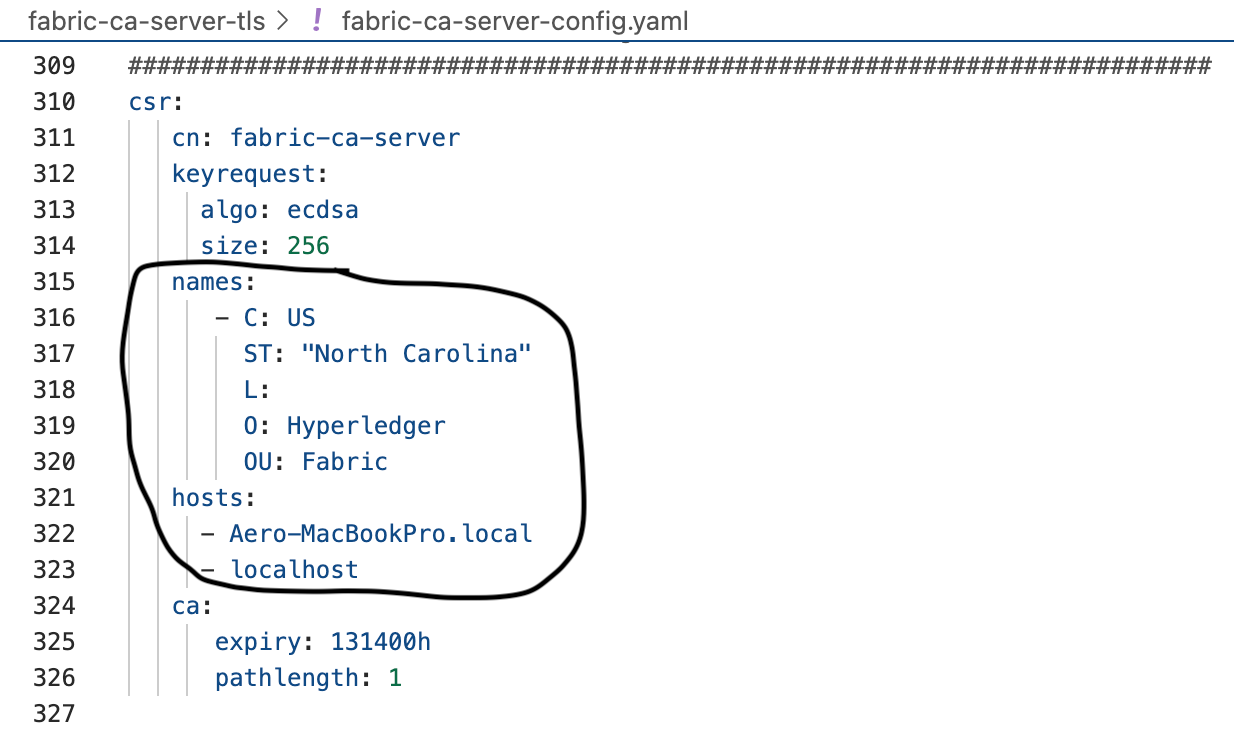
The 5th one is csr.hosts. I'm using my local machine for illustrative purposes. Update this parameter to include a hostname, ip address, or domain name where this server is running, if it is different than what is already in this file.
The last one is signing.profiles.ca. Remove the ca section. The signing.profiles block should only contain tls profile, since this is a TLS-CA-server that will not issue CA certificates.
Step 15: Start the TLS-CA-server
Since you just modified the values in the csr block of the configuration, you need to delete the fabric-ca-server-tls/ca-cert.pem file and the entire fabric-ca-server-tls/msp folder. The certificate and folder will be regenerated when you start the server. So:
rm -rf ca-cert.pem msp
Your fabric-ca-server-tls directory will be left with these artifacts:
Everything is clean. You can kick start the server now:
fabric-ca-server start
Listening on the default port https://0.0.0.0:7054. More details:
Terminal (TLS-CA-server)
2023/03/17 17:39:38 [INFO] Configuration file location: /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-server-tls/fabric-ca-server-config.yaml
2023/03/17 17:39:38 [INFO] Starting server in home directory: /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-server-tls
2023/03/17 17:39:38 [INFO] Server Version: 1.5.5
2023/03/17 17:39:38 [INFO] Server Levels: &{Identity:2 Affiliation:1 Certificate:1 Credential:1 RAInfo:1 Nonce:1}
2023/03/17 17:39:38 [WARNING] &{69 The specified CA certificate file /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-server-tls/ca-cert.pem does not exist}
2023/03/17 17:39:38 [INFO] generating key: &{A:ecdsa S:256}
2023/03/17 17:39:38 [INFO] encoded CSR
2023/03/17 17:39:38 [INFO] signed certificate with serial number 666462293628534400276457273327095415719290606859
2023/03/17 17:39:38 [INFO] The CA key and certificate were generated for CA tls-ca
2023/03/17 17:39:38 [INFO] The key was stored by BCCSP provider 'SW'
2023/03/17 17:39:38 [INFO] The certificate is at: /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-server-tls/ca-cert.pem
2023/03/17 17:39:38 [INFO] Initialized sqlite3 database at /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-server-tls/fabric-ca-server.db
2023/03/17 17:39:38 [INFO] The issuer key was successfully stored. The public key is at: /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-server-tls/IssuerPublicKey, secret key is at: /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-server-tls/msp/keystore/IssuerSecretKey
2023/03/17 17:39:38 [INFO] Idemix issuer revocation public and secret keys were generated for CA 'tls-ca'
2023/03/17 17:39:38 [INFO] The revocation key was successfully stored. The public key is at: /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-server-tls/IssuerRevocationPublicKey, private key is at: /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-server-tls/msp/keystore/IssuerRevocationPrivateKey
2023/03/17 17:39:38 [INFO] Home directory for default CA: /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-server-tls
2023/03/17 17:39:38 [INFO] Operation Server Listening on 127.0.0.1:9443
2023/03/17 17:39:38 [INFO] generating key: &{A:ecdsa S:256}
2023/03/17 17:39:38 [INFO] encoded CSR
2023/03/17 17:39:38 [INFO] signed certificate with serial number 203687874106044434678470980322993655539029891391
2023/03/17 17:39:38 [INFO] Listening on https://0.0.0.0:7054
The server is up and running. Let's open another pane in your terminal and have a look what else you got from starting the server.

ca-cert.pem certificate and the entire msp folder are regenerated. And a tls-cert.pem is added.
Step 16: Set up the TLS-CA-client
Now that your TLS-CA-server is configured. Before you can deploy any other nodes for your organization(s), you need to enroll the bootstrap admin of the TLS-CA-server. Since the server is up and running, you need to have a TLS-CA-client to communicate with it.
Go over to the root level of {Your fabric-samples repo}. And create the fabric-ca-client folder as the base of TLS-CA-client:
mkdir fabric-ca-client
Go in the newly created directory.
cd fabric-ca-client
Copy the fabric-ca-client binary and paste into it.
And create four folders.
mkdir tls-ca org1-ca int-ca tls-root-cert
The directory will end up having one binary and four folders:
fabric-ca-client ├── fabric-ca-client ├── int-ca ├── org1-ca ├── tls-ca └── tls-root-cert
And the fabric-ca-client binary will become the interface for you to interact with the TLS-CA-server to execute command.
Create sub-folders for each CA-server is a best practice, as it can store the certificates generated later on in partitions. The three folders int-ca, org1-ca, and tls-ca are for certificate management. Because you will use a single TLS-CA-client, the fabric-ca-client, to submit register and enrollment requests to multiple Organization-CAs.
In terms of the tls-root-cert folder, on the other hand, is for the layer of TLS communication. Every time the TLS-CA-client transacts with a Organization-CA-server, e.g.: org1-ca, it needs to provide the TLS-CA-server the “root certificate” to secure the client-server communication. Hence, you need to have a tls-root-cert sub-folder to store the root certificate.
Go over to the folder fabric-ca-server-tls, make a copy of ca-cert.pem (the root certificate), paste it into the fabric-ca-client/tls-root-cert folder, and rename it as tls-ca-cert.pem to make it clear this is the root certificate from the TLS-CA-server for the TLS usage:
Your TLS-CA-client is now well set up, sitting alongside the TLS-CA-server. Let's configure your machine to let your TLS-CA-client knows where the fabric-ca-client binary is located. Set the environment varaible:
export FABRIC_CA_CLIENT_HOME={Your fabric-samples repo}/fabric-ca-clientStep 17: Enroll the TLS-CA-server bootstrap admin
You can now deploy other nodes, such as: Organization-CA, but you need to enroll the bootstrap admin of TLS-CA-server first. Let's do it with the newly setup TLS-CA-client. Inside the directory {Your fabric-samples repo}/fabric-ca-client, execute the fabric-ca-client binary with the command:
fabric-ca-client enroll -d -u https://tls-admin:tls-adminpw@localhost:7054 --tls.certfiles tls-root-cert/tls-ca-cert.pem --mspdir tls-ca/tlsadmin/msp
The TLS-CA-server will return a response enroll 201 0 "OK". The fabric-ca-client/tls-ca/tlsadmin/msp folder will be generated and contains the signed cert and private key for the TLS-CA-server bootstrap admin. More details:
Terminal (TLS-CA-client)
2023/03/18 10:33:57 [DEBUG] Set log level:
2023/03/18 10:33:57 [DEBUG] Home directory: /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-client
2023/03/18 10:33:57 [INFO] Created a default configuration file at /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-client/fabric-ca-client-config.yaml
2023/03/18 10:33:57 [DEBUG] Client configuration settings: &{URL:https://tls-admin:tls-adminpw@localhost:7054 MSPDir:tls-ca/tlsadmin/msp TLS:{Enabled:true CertFiles:[tls-root-cert/tls-ca-cert.pem] Client:{KeyFile: CertFile:}} Enrollment:{ Name: Secret:**** CAName: AttrReqs:[] Profile: Label: CSR:<nil> Type:x509 } CSR:{CN:tls-admin Names:[{C:US ST:North Carolina L: O:Hyperledger OU:Fabric SerialNumber:}] Hosts:[Aero-MacBookPro.local] KeyRequest:0xc0002e3660 CA:<nil> SerialNumber:} ID:{Name: Type:client Secret: MaxEnrollments:0 Affiliation: Attributes:[] CAName:} Revoke:{Name: Serial: AKI: Reason: CAName: GenCRL:false} CAInfo:{CAName:} CAName: CSP:0xc0002e39e0 Debug:true LogLevel: Idemix:{Curve:amcl.Fp256bn}}
2023/03/18 10:33:57 [DEBUG] Entered runEnroll
2023/03/18 10:33:57 [DEBUG] Enrolling { Name:tls-admin Secret:**** CAName: AttrReqs:[] Profile: Label: CSR:&{tls-admin [{US North Carolina Hyperledger Fabric }] [Aero-MacBookPro.local] 0xc0002e3660 <nil> } Type:x509 }
2023/03/18 10:33:57 [DEBUG] Initializing client with config: &{URL:https://localhost:7054 MSPDir:tls-ca/tlsadmin/msp TLS:{Enabled:true CertFiles:[tls-root-cert/tls-ca-cert.pem] Client:{KeyFile: CertFile:}} Enrollment:{ Name:tls-admin Secret:**** CAName: AttrReqs:[] Profile: Label: CSR:&{tls-admin [{US North Carolina Hyperledger Fabric }] [Aero-MacBookPro.local] 0xc0002e3660 <nil> } Type:x509 } CSR:{CN:tls-admin Names:[{C:US ST:North Carolina L: O:Hyperledger OU:Fabric SerialNumber:}] Hosts:[Aero-MacBookPro.local] KeyRequest:0xc0002e3660 CA:<nil> SerialNumber:} ID:{Name: Type:client Secret: MaxEnrollments:0 Affiliation: Attributes:[] CAName:} Revoke:{Name: Serial: AKI: Reason: CAName: GenCRL:false} CAInfo:{CAName:} CAName: CSP:0xc0002e39e0 Debug:true LogLevel: Idemix:{Curve:amcl.Fp256bn}}
2023/03/18 10:33:57 [DEBUG] Initializing BCCSP: &{ProviderName:SW SwOpts:0xc00010db30 PluginOpts:<nil>}
2023/03/18 10:33:57 [DEBUG] Initializing BCCSP with software options &{SecLevel:256 HashFamily:SHA2 FileKeystore:0xc00015da20 DummyKeystore:<nil> InmemKeystore:<nil>}
2023/03/18 10:33:57 [INFO] TLS Enabled
2023/03/18 10:33:57 [DEBUG] CA Files: [/Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-client/tls-root-cert/tls-ca-cert.pem]
2023/03/18 10:33:57 [DEBUG] Client Cert File:
2023/03/18 10:33:57 [DEBUG] Client Key File:
2023/03/18 10:33:57 [DEBUG] Client TLS certificate and/or key file not provided
2023/03/18 10:33:57 [DEBUG] Using curve amcl.Fp256bn for Idemix
2023/03/18 10:33:57 [DEBUG] GenCSR &{CN:tls-admin Names:[{C:US ST:North Carolina L: O:Hyperledger OU:Fabric SerialNumber:}] Hosts:[Aero-MacBookPro.local] KeyRequest:0xc0002e3660 CA:<nil> SerialNumber:}
2023/03/18 10:33:57 [INFO] generating key: &{A:ecdsa S:256}
2023/03/18 10:33:57 [DEBUG] generate key from request: algo=ecdsa, size=256
2023/03/18 10:33:57 [INFO] encoded CSR
2023/03/18 10:33:57 [DEBUG] Sending request
POST https://localhost:7054/enroll
{"hosts":["Aero-MacBookPro.local"],"certificate_request":"-----BEGIN CERTIFICATE REQUEST-----\nMIIBTzCB9gIBADBhMQswCQYDVQQGEwJVUzEXMBUGA1UECBMOTm9ydGggQ2Fyb2xp\nbmExFDASBgNVBAoTC0h5cGVybGVkZ2VyMQ8wDQYDVQQLEwZGYWJyaWMxEjAQBgNV\nBAMTCXRscy1hZG1pbjBZMBMGByqGSM49AgEGCCqGSM49AwEHA0IABIv7UquVpKui\ns+1xJyx4Bc+jNDRUgkATqMD83j78FIoHjdrKUm0w479SiT1ormgcQXdnIHHCSJ9F\nVrPvbfyBY2KgMzAxBgkqhkiG9w0BCQ4xJDAiMCAGA1UdEQQZMBeCFUFlcm8tTWFj\nQm9va1Byby5sb2NhbDAKBggqhkjOPQQDAgNIADBFAiEAhyb9CP7F6PartrGdZYxL\n6F52OPPg9Lm+XtdeSatTw2oCIGM0tnb6jkXgDT+TFiLLKAdK5xhjQQo00EyNtnx7\ngxjQ\n-----END CERTIFICATE REQUEST-----\n","profile":"","crl_override":"","label":"","NotBefore":"0001-01-01T00:00:00Z","NotAfter":"0001-01-01T00:00:00Z","ReturnPrecert":false,"CAName":""}
2023/03/18 10:33:57 [DEBUG] Received response
statusCode=201 (201 Created)
2023/03/18 10:33:57 [DEBUG] Response body result: map[Cert:LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUNUakNDQWZXZ0F3SUJBZ0lVYldkZFlYMzN6b2JOeGczTGNvK0lYZUo1eWpJd0NnWUlLb1pJemowRUF3SXcKYURFTE1Ba0dBMVVFQmhNQ1ZWTXhGekFWQmdOVkJBZ1REazV2Y25Sb0lFTmhjbTlzYVc1aE1SUXdFZ1lEVlFRSwpFd3RJZVhCbGNteGxaR2RsY2pFUE1BMEdBMVVFQ3hNR1JtRmljbWxqTVJrd0Z3WURWUVFERXhCbVlXSnlhV010ClkyRXRjMlZ5ZG1WeU1CNFhEVEl6TURNeE9EQXlNall3TUZvWERUSTBNRE14TnpBeU16UXdNRm93WVRFTE1Ba0cKQTFVRUJoTUNWVk14RnpBVkJnTlZCQWdURGs1dmNuUm9JRU5oY205c2FXNWhNUlF3RWdZRFZRUUtFd3RJZVhCbApjbXhsWkdkbGNqRVBNQTBHQTFVRUN4TUdZMnhwWlc1ME1SSXdFQVlEVlFRREV3bDBiSE10WVdSdGFXNHdXVEFUCkJnY3Foa2pPUFFJQkJnZ3Foa2pPUFFNQkJ3TkNBQVNMKzFLcmxhU3JvclB0Y1Njc2VBWFBvelEwVklKQUU2akEKL040Ky9CU0tCNDNheWxKdE1PTy9Vb2s5YUs1b0hFRjNaeUJ4d2tpZlJWYXo3MjM4Z1dOaW80R0RNSUdBTUE0RwpBMVVkRHdFQi93UUVBd0lIZ0RBTUJnTlZIUk1CQWY4RUFqQUFNQjBHQTFVZERnUVdCQlJWK1JMeGFtSEhNMEVPCm9zYlV1QWNrSytjYlBqQWZCZ05WSFNNRUdEQVdnQlFMb1hYbDZzbzBsSTZZZTFSRVg3WFVWNHBtVVRBZ0JnTlYKSFJFRUdUQVhnaFZCWlhKdkxVMWhZMEp2YjJ0UWNtOHViRzlqWVd3d0NnWUlLb1pJemowRUF3SURSd0F3UkFJZwpKVjNjeVIva0Z0bk11MGU3ZjBDUTcvLy9sWjU2NlZpNHZLWG1vdTJLeGpBQ0lIeFJmaW82RHhtTVdqTTNBZ0xvCitoM1QwTkFzbFg4MTRYQkVOZmZaeEtncQotLS0tLUVORCBDRVJUSUZJQ0FURS0tLS0tCg== ServerInfo:map[CAChain:LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUNGekNDQWIyZ0F3SUJBZ0lVQTR6am9jb1d5MGtwaklGM0NkTFV4eGJ2UklVd0NnWUlLb1pJemowRUF3SXcKYURFTE1Ba0dBMVVFQmhNQ1ZWTXhGekFWQmdOVkJBZ1REazV2Y25Sb0lFTmhjbTlzYVc1aE1SUXdFZ1lEVlFRSwpFd3RJZVhCbGNteGxaR2RsY2pFUE1BMEdBMVVFQ3hNR1JtRmljbWxqTVJrd0Z3WURWUVFERXhCbVlXSnlhV010ClkyRXRjMlZ5ZG1WeU1CNFhEVEl6TURNeE9EQXlNall3TUZvWERUTTRNRE14TkRBeU1qWXdNRm93YURFTE1Ba0cKQTFVRUJoTUNWVk14RnpBVkJnTlZCQWdURGs1dmNuUm9JRU5oY205c2FXNWhNUlF3RWdZRFZRUUtFd3RJZVhCbApjbXhsWkdkbGNqRVBNQTBHQTFVRUN4TUdSbUZpY21sak1Sa3dGd1lEVlFRREV4Qm1ZV0p5YVdNdFkyRXRjMlZ5CmRtVnlNRmt3RXdZSEtvWkl6ajBDQVFZSUtvWkl6ajBEQVFjRFFnQUVQUXl3VnRnWkF0THBQd29oTEIvMDkwUDEKdmlFRmtMRFEvRkNJYXJidVVGQVovTWNlV0JKQlNkS0VPUTdBNlZSOUZsZkpZcjZCNVB5RkJya2RsWkYyRktORgpNRU13RGdZRFZSMFBBUUgvQkFRREFnRUdNQklHQTFVZEV3RUIvd1FJTUFZQkFmOENBUUV3SFFZRFZSME9CQllFCkZBdWhkZVhxeWpTVWpwaDdWRVJmdGRSWGltWlJNQW9HQ0NxR1NNNDlCQU1DQTBnQU1FVUNJUUNrMDJNZWdiUnoKQ2tCRFdia3g1UUtEcHplUitoeUJEdXRLNjdhODhpcVJaZ0lnUlZ6RXNHOEtCMy9vcEZEblA5Qk9DSEZQSEowTgo4N25EK1BkK1lOU1ZRR009Ci0tLS0tRU5EIENFUlRJRklDQVRFLS0tLS0K CAName:tls-ca IssuerPublicKey:CgJPVQoEUm9sZQoMRW5yb2xsbWVudElEChBSZXZvY2F0aW9uSGFuZGxlEkQKIPP0hMkP/e2EoHIDbRmrZJypG9o5zRFkVfZuBGSZUpTbEiCgydtTkJpTo/uu8X4cCkTqnXaqEoSXZrGhbG+2QY2nexpECiC7rjjDA8roheGkDAlTeV+5SDU1yDVia+P6yVXQyjXiexIgS2dE7l1u6Kfjma09tWZAe0TuwdxLcnS8du5PUGPn8fwiRAogNo21bukSuGl4FiNwVUXT8/5N+/T+8JDXNyKuh9ikfbgSIJdR6G4OMXzkF8gLds2QT60XLRF1RiXJ5f6IDG/41YUcIkQKICLwGYD+diqCUWtD0ONKEbvXr3R62/qNtDVVzKE2558vEiALlzfEjdAtnbybfHqPvx6fcLbxd1qTeDLi8Zn3tbKS/iJECiAI49gFcnMKEJKDGkeXtuhUMoEGK9hJWaHAvxObYiTnoRIgWQ5XPQ2EnhSlyEPLPXLuCRcGe1EsoiCELgqLhbApggIiRAogIXzXFn2NLXEaKBEYZNXj/Z01RteIpqqARJ5erJYoLYcSIHtgl1fzd7RXh7jNG1Ye+z9JRZb3LrshO5CRDrjELg5eKogBCiAjYmkBKbq2tWOUvwi6WZOz4mW4aInIFl60PCPzhXHoqhIgD1zx7CmwlRRNOI24zRFZMzDTYG92GYleShOwtmuCWcMaIDF5gLNYX4a1dwre5w0giU9bb+k4WD/lgZolY3FuFa8TIiDMC5sLCyThq2vtZJjW+uFIccuq7sgjc5PUKucYQ2TklDJECiAntdSO9QeY8uke357QSLs4Mv8A8q/mbSr9BarcZJR0CRIgD4ccwRF4J8NAzDr6cZJ+aMRK/Dq/sNdWC612WamAk/46RAogPkU57sx8P5+s9Yeei8wBQZxqRs+x8E8fbUZY7bFKEDgSIFUa7lXZCaTSOh9O0zoHrAw99uCpQe/wQVvuczXYxW/uQiDzQ/nT52EcQdB3vfG1U/1Z7YSuy8Hn5XNb11qCE0tBrUogsTmgcvmR0F5JM7cX85ysJfQMVRaF9ACGPbY+16RZKdhSIB4I31hGSuqG2vCVM9sLb27FpekfKaoO1prLt2ynCJiC IssuerRevocationPublicKey:LS0tLS1CRUdJTiBQVUJMSUMgS0VZLS0tLS0KTUhZd0VBWUhLb1pJemowQ0FRWUZLNEVFQUNJRFlnQUVuN1N4cjlzUytaWERJdjFoWUNuQjZEVGg2Z1p2RlZsNApXeFU0aVIwWDhMUHd5eCtnUjdMOXJSdytubGc1REFqMS9sdmtoWFltS1Z6NlowekdIZWlLSm5HS1lVcXlnditpCmliSXRFc1Q4Wkc0K0FJWjc2Wnh3RXM2UktYdnNiQUxSCi0tLS0tRU5EIFBVQkxJQyBLRVktLS0tLQo= Version:]]
2023/03/18 10:33:57 [DEBUG] newEnrollmentResponse tls-admin
2023/03/18 10:33:57 [INFO] Stored client certificate at /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-client/tls-ca/tlsadmin/msp/signcerts/cert.pem
2023/03/18 10:33:57 [INFO] Stored root CA certificate at /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-client/tls-ca/tlsadmin/msp/cacerts/localhost-7054.pem
2023/03/18 10:33:57 [INFO] Stored Issuer public key at /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-client/tls-ca/tlsadmin/msp/IssuerPublicKey
2023/03/18 10:33:57 [INFO] Stored Issuer revocation public key at /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-client/tls-ca/tlsadmin/msp/IssuerRevocationPublicKey
Terminal (TLS-CA-server)
2023/03/18 10:33:57 [INFO] signed certificate with serial number 624585105392668593012768528794172529426508139058
2023/03/18 10:33:57 [INFO] [::1]:50026 POST /enroll 201 0 "OK"
Step 18: Register and enroll the Organization-CA-server bootstrap admin
An identity is encapsulated in an X.509 digital certificate in the Hyperledger Fabric blockchain network. The identity is the prerequisite for a role to acquire a TLS certificate.
Orderer, Peer, Organization-CA, etc. No matter what role they have within an organization, each node that will transact on the network needs to be registered with the TLS-CA-server for an identity, so that they can enroll to get their TLS certificates.
The TLS-CA-server bootstrap admin created in the previous step is also an idendtity. It has full admin privileges for the TLS-CA-server. One of its key abilities is to register new identities. To set up an Organization-CA node, you need to register the Organization-CA bootstrap admin identity with the TLS-CA-server first.
Let's perform the registration process with the TLS-CA-client:
fabric-ca-client register -d --id.name rcaadmin --id.secret rcaadminpw -u https://localhost:7054 --tls.certfiles tls-root-cert/tls-ca-cert.pem --mspdir tls-ca/tlsadmin/msp
Once again, you can use whatever name and password you like in the identity creation. Or else, if you follow the tutorial rigorously, an Organization-CA bootstrap admin with name rcaadmin and password rcaadminpw is just created. And the CA-server will return a response register 201 0 "OK". More details:
Terminal (TLS-CA-client)
2023/03/18 10:35:58 [DEBUG] Set log level:
2023/03/18 10:35:58 [DEBUG] Home directory: /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-client
2023/03/18 10:35:58 [INFO] Configuration file location: /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-client/fabric-ca-client-config.yaml
2023/03/18 10:35:58 [DEBUG] Checking for enrollment
2023/03/18 10:35:58 [DEBUG] Initializing client with config: &{URL:https://localhost:7054 MSPDir:tls-ca/tlsadmin/msp TLS:{Enabled:true CertFiles:[tls-root-cert/tls-ca-cert.pem] Client:{KeyFile: CertFile:}} Enrollment:{ Name: Secret:**** CAName: AttrReqs:[] Profile: Label: CSR:<nil> Type:x509 } CSR:{CN:tls-admin Names:[{C:US ST:North Carolina L: O:Hyperledger OU:Fabric SerialNumber:}] Hosts:[Aero-MacBookPro.local] KeyRequest:0xc0002b1ae0 CA:<nil> SerialNumber:} ID:{Name:rcaadmin Type:client Secret:rcaadminpw MaxEnrollments:0 Affiliation: Attributes:[] CAName:} Revoke:{Name: Serial: AKI: Reason: CAName: GenCRL:false} CAInfo:{CAName:} CAName: CSP:0xc0002b1e60 Debug:true LogLevel: Idemix:{Curve:amcl.Fp256bn}}
2023/03/18 10:35:58 [DEBUG] Initializing BCCSP: &{ProviderName:SW SwOpts:0xc0000df410 PluginOpts:<nil>}
2023/03/18 10:35:58 [DEBUG] Initializing BCCSP with software options &{SecLevel:256 HashFamily:SHA2 FileKeystore:0xc0001273e0 DummyKeystore:<nil> InmemKeystore:<nil>}
2023/03/18 10:35:58 [INFO] TLS Enabled
2023/03/18 10:35:58 [DEBUG] CA Files: [/Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-client/tls-root-cert/tls-ca-cert.pem]
2023/03/18 10:35:58 [DEBUG] Client Cert File:
2023/03/18 10:35:58 [DEBUG] Client Key File:
2023/03/18 10:35:58 [DEBUG] Client TLS certificate and/or key file not provided
2023/03/18 10:35:58 [DEBUG] Using curve amcl.Fp256bn for Idemix
2023/03/18 10:35:58 [DEBUG] CheckIdemixEnrollment - ipkFile: /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-client/tls-ca/tlsadmin/msp/IssuerPublicKey, idemixCredFile: /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-client/tls-ca/tlsadmin/msp/user/SignerConfig
2023/03/18 10:35:58 [DEBUG] Client configuration settings: &{URL:https://localhost:7054 MSPDir:/Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-client/tls-ca/tlsadmin/msp TLS:{Enabled:true CertFiles:[/Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-client/tls-root-cert/tls-ca-cert.pem] Client:{KeyFile: CertFile:}} Enrollment:{ Name: Secret:**** CAName: AttrReqs:[] Profile: Label: CSR:<nil> Type:x509 } CSR:{CN:tls-admin Names:[{C:US ST:North Carolina L: O:Hyperledger OU:Fabric SerialNumber:}] Hosts:[Aero-MacBookPro.local] KeyRequest:0xc0002b1ae0 CA:<nil> SerialNumber:} ID:{Name:rcaadmin Type:client Secret:rcaadminpw MaxEnrollments:0 Affiliation: Attributes:[] CAName:} Revoke:{Name: Serial: AKI: Reason: CAName: GenCRL:false} CAInfo:{CAName:} CAName: CSP:0xc0002b1e60 Debug:true LogLevel: Idemix:{Curve:amcl.Fp256bn}}
2023/03/18 10:35:58 [DEBUG] Entered runRegister
2023/03/18 10:35:58 [DEBUG] Initializing client with config: &{URL:https://localhost:7054 MSPDir:/Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-client/tls-ca/tlsadmin/msp TLS:{Enabled:true CertFiles:[/Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-client/tls-root-cert/tls-ca-cert.pem] Client:{KeyFile: CertFile:}} Enrollment:{ Name: Secret:**** CAName: AttrReqs:[] Profile: Label: CSR:<nil> Type:x509 } CSR:{CN:tls-admin Names:[{C:US ST:North Carolina L: O:Hyperledger OU:Fabric SerialNumber:}] Hosts:[Aero-MacBookPro.local] KeyRequest:0xc0002b1ae0 CA:<nil> SerialNumber:} ID:{Name:rcaadmin Type:client Secret:rcaadminpw MaxEnrollments:0 Affiliation: Attributes:[] CAName:} Revoke:{Name: Serial: AKI: Reason: CAName: GenCRL:false} CAInfo:{CAName:} CAName: CSP:0xc0002b1e60 Debug:true LogLevel: Idemix:{Curve:amcl.Fp256bn}}
2023/03/18 10:35:58 [DEBUG] Initializing BCCSP: &{ProviderName:SW SwOpts:0xc0000df410 PluginOpts:<nil>}
2023/03/18 10:35:58 [DEBUG] Initializing BCCSP with software options &{SecLevel:256 HashFamily:SHA2 FileKeystore:0xc0001273e0 DummyKeystore:<nil> InmemKeystore:<nil>}
2023/03/18 10:35:58 [INFO] TLS Enabled
2023/03/18 10:35:58 [DEBUG] CA Files: [/Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-client/tls-root-cert/tls-ca-cert.pem]
2023/03/18 10:35:58 [DEBUG] Client Cert File:
2023/03/18 10:35:58 [DEBUG] Client Key File:
2023/03/18 10:35:58 [DEBUG] Client TLS certificate and/or key file not provided
2023/03/18 10:35:58 [DEBUG] Using curve amcl.Fp256bn for Idemix
2023/03/18 10:35:58 [DEBUG] Loading identity: keyFile=/Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-client/tls-ca/tlsadmin/msp/keystore/key.pem, certFile=/Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-client/tls-ca/tlsadmin/msp/signcerts/cert.pem
2023/03/18 10:35:58 [DEBUG] No credential found at /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-client/tls-ca/tlsadmin/msp/user/SignerConfig: open /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-client/tls-ca/tlsadmin/msp/user/SignerConfig: no such file or directory
2023/03/18 10:35:58 [DEBUG] No Idemix credential found at /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-client/tls-ca/tlsadmin/msp/user/SignerConfig
2023/03/18 10:35:58 [DEBUG] Register { Name:rcaadmin Type:client Secret:**** MaxEnrollments:0 Affiliation: Attributes:[] CAName: }
2023/03/18 10:35:58 [DEBUG] Adding token-based authorization header
2023/03/18 10:35:58 [DEBUG] Sending request
POST https://localhost:7054/register
{"id":"rcaadmin","type":"client","secret":"rcaadminpw","affiliation":""}
2023/03/18 10:35:58 [DEBUG] Received response
statusCode=201 (201 Created)
2023/03/18 10:35:58 [DEBUG] Response body result: map[secret:rcaadminpw]
2023/03/18 10:35:58 [DEBUG] The register request completed successfully
Password: rcaadminpw
Terminal (TLS-CA-server)
2023/03/18 10:35:58 [INFO] [::1]:50029 POST /register 201 0 "OK"
Prerequisite fulfilled. Let's enroll the Organization-CA bootstrap admin rcaadmin:
fabric-ca-client enroll -d -u https://rcaadmin:rcaadminpw@localhost:7054 --tls.certfiles tls-root-cert/tls-ca-cert.pem --csr.hosts 'localhost' --mspdir tls-ca/rcaadmin/msp
Both TLS certificate and private key for rcaadmin are generated. More details:
Terminal (TLS-CA-client)
2023/03/18 10:38:32 [DEBUG] Set log level:
2023/03/18 10:38:32 [DEBUG] Home directory: /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-client
2023/03/18 10:38:32 [DEBUG] Client configuration settings: &{URL:https://rcaadmin:rcaadminpw@localhost:7054 MSPDir:tls-ca/rcaadmin/msp TLS:{Enabled:true CertFiles:[tls-root-cert/tls-ca-cert.pem] Client:{KeyFile: CertFile:}} Enrollment:{ Name: Secret:**** CAName: AttrReqs:[] Profile: Label: CSR:<nil> Type:x509 } CSR:{CN:tls-admin Names:[{C:US ST:North Carolina L: O:Hyperledger OU:Fabric SerialNumber:}] Hosts:[localhost] KeyRequest:0xc0003117a0 CA:<nil> SerialNumber:} ID:{Name: Type:client Secret: MaxEnrollments:0 Affiliation: Attributes:[] CAName:} Revoke:{Name: Serial: AKI: Reason: CAName: GenCRL:false} CAInfo:{CAName:} CAName: CSP:0xc000311b20 Debug:true LogLevel: Idemix:{Curve:amcl.Fp256bn}}
2023/03/18 10:38:32 [DEBUG] Entered runEnroll
2023/03/18 10:38:32 [DEBUG] Enrolling { Name:rcaadmin Secret:**** CAName: AttrReqs:[] Profile: Label: CSR:&{tls-admin [{US North Carolina Hyperledger Fabric }] [localhost] 0xc0003117a0 <nil> } Type:x509 }
2023/03/18 10:38:32 [DEBUG] Initializing client with config: &{URL:https://localhost:7054 MSPDir:tls-ca/rcaadmin/msp TLS:{Enabled:true CertFiles:[tls-root-cert/tls-ca-cert.pem] Client:{KeyFile: CertFile:}} Enrollment:{ Name:rcaadmin Secret:**** CAName: AttrReqs:[] Profile: Label: CSR:&{tls-admin [{US North Carolina Hyperledger Fabric }] [localhost] 0xc0003117a0 <nil> } Type:x509 } CSR:{CN:tls-admin Names:[{C:US ST:North Carolina L: O:Hyperledger OU:Fabric SerialNumber:}] Hosts:[localhost] KeyRequest:0xc0003117a0 CA:<nil> SerialNumber:} ID:{Name: Type:client Secret: MaxEnrollments:0 Affiliation: Attributes:[] CAName:} Revoke:{Name: Serial: AKI: Reason: CAName: GenCRL:false} CAInfo:{CAName:} CAName: CSP:0xc000311b20 Debug:true LogLevel: Idemix:{Curve:amcl.Fp256bn}}
2023/03/18 10:38:32 [DEBUG] Initializing BCCSP: &{ProviderName:SW SwOpts:0xc0000fa8a0 PluginOpts:<nil>}
2023/03/18 10:38:32 [DEBUG] Initializing BCCSP with software options &{SecLevel:256 HashFamily:SHA2 FileKeystore:0xc00011b700 DummyKeystore:<nil> InmemKeystore:<nil>}
2023/03/18 10:38:32 [INFO] TLS Enabled
2023/03/18 10:38:32 [DEBUG] CA Files: [/Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-client/tls-root-cert/tls-ca-cert.pem]
2023/03/18 10:38:32 [DEBUG] Client Cert File:
2023/03/18 10:38:32 [DEBUG] Client Key File:
2023/03/18 10:38:32 [DEBUG] Client TLS certificate and/or key file not provided
2023/03/18 10:38:32 [DEBUG] Using curve amcl.Fp256bn for Idemix
2023/03/18 10:38:32 [DEBUG] GenCSR &{CN:tls-admin Names:[{C:US ST:North Carolina L: O:Hyperledger OU:Fabric SerialNumber:}] Hosts:[localhost] KeyRequest:0xc0003117a0 CA:<nil> SerialNumber:}
2023/03/18 10:38:32 [INFO] generating key: &{A:ecdsa S:256}
2023/03/18 10:38:32 [DEBUG] generate key from request: algo=ecdsa, size=256
2023/03/18 10:38:32 [INFO] encoded CSR
2023/03/18 10:38:32 [DEBUG] Sending request
POST https://localhost:7054/enroll
{"hosts":["localhost"],"certificate_request":"-----BEGIN CERTIFICATE REQUEST-----\nMIIBQjCB6QIBADBgMQswCQYDVQQGEwJVUzEXMBUGA1UECBMOTm9ydGggQ2Fyb2xp\nbmExFDASBgNVBAoTC0h5cGVybGVkZ2VyMQ8wDQYDVQQLEwZGYWJyaWMxETAPBgNV\nBAMTCHJjYWFkbWluMFkwEwYHKoZIzj0CAQYIKoZIzj0DAQcDQgAEFHjAU/QIREiP\nEJELXHvxSA4dhjdWYdg7mxIDBp7E80Vf5jPSs/e0rZ/uUl08pzGFwbbn+AYpJ3W+\nbBLv4VRGWaAnMCUGCSqGSIb3DQEJDjEYMBYwFAYDVR0RBA0wC4IJbG9jYWxob3N0\nMAoGCCqGSM49BAMCA0gAMEUCIQDvf2pvMe9/awxF0KTbu9OHIDGi8UHV8/fFRtdr\nKRTTRwIgeUdptVYybsfL8qTKaQiITzqJn82jDZDq4G0vwzPIDS4=\n-----END CERTIFICATE REQUEST-----\n","profile":"","crl_override":"","label":"","NotBefore":"0001-01-01T00:00:00Z","NotAfter":"0001-01-01T00:00:00Z","ReturnPrecert":false,"CAName":""}
2023/03/18 10:38:32 [DEBUG] Received response
statusCode=201 (201 Created)
2023/03/18 10:38:32 [DEBUG] Response body result: map[Cert:LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUNuekNDQWtXZ0F3SUJBZ0lVSC9qRW9UbS9tZjRGRlRqdzQ5S3BSZ0FLZ1JJd0NnWUlLb1pJemowRUF3SXcKYURFTE1Ba0dBMVVFQmhNQ1ZWTXhGekFWQmdOVkJBZ1REazV2Y25Sb0lFTmhjbTlzYVc1aE1SUXdFZ1lEVlFRSwpFd3RJZVhCbGNteGxaR2RsY2pFUE1BMEdBMVVFQ3hNR1JtRmljbWxqTVJrd0Z3WURWUVFERXhCbVlXSnlhV010ClkyRXRjMlZ5ZG1WeU1CNFhEVEl6TURNeE9EQXlNall3TUZvWERUSTBNRE14TnpBeU16a3dNRm93WURFTE1Ba0cKQTFVRUJoTUNWVk14RnpBVkJnTlZCQWdURGs1dmNuUm9JRU5oY205c2FXNWhNUlF3RWdZRFZRUUtFd3RJZVhCbApjbXhsWkdkbGNqRVBNQTBHQTFVRUN4TUdZMnhwWlc1ME1SRXdEd1lEVlFRREV3aHlZMkZoWkcxcGJqQlpNQk1HCkJ5cUdTTTQ5QWdFR0NDcUdTTTQ5QXdFSEEwSUFCQlI0d0ZQMENFUklqeENSQzF4NzhVZ09IWVkzVm1IWU81c1MKQXdhZXhQTkZYK1l6MHJQM3RLMmY3bEpkUEtjeGhjRzI1L2dHS1NkMXZtd1M3K0ZVUmxtamdkUXdnZEV3RGdZRApWUjBQQVFIL0JBUURBZ2VBTUF3R0ExVWRFd0VCL3dRQ01BQXdIUVlEVlIwT0JCWUVGRzB0UHgrd01tdVl2a3FPCmFxalN5dUc0RXJzbk1COEdBMVVkSXdRWU1CYUFGQXVoZGVYcXlqU1VqcGg3VkVSZnRkUlhpbVpSTUJRR0ExVWQKRVFRTk1BdUNDV3h2WTJGc2FHOXpkREJiQmdncUF3UUZCZ2NJQVFSUGV5SmhkSFJ5Y3lJNmV5Sm9aaTVCWm1acApiR2xoZEdsdmJpSTZJaUlzSW1obUxrVnVjbTlzYkcxbGJuUkpSQ0k2SW5KallXRmtiV2x1SWl3aWFHWXVWSGx3ClpTSTZJbU5zYVdWdWRDSjlmVEFLQmdncWhrak9QUVFEQWdOSUFEQkZBaUVBazU1ekV0clRFMFI1TmI3bElJbVoKTC9SaWtacTdnRUZVbEJmT0R5MHNCdGtDSUFmd0pDOVc2ODV0V3Z5VmRPblorY0RMYkwwREdQY0FhL3JYZC9LYQo2SWpuCi0tLS0tRU5EIENFUlRJRklDQVRFLS0tLS0K ServerInfo:map[CAChain:LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUNGekNDQWIyZ0F3SUJBZ0lVQTR6am9jb1d5MGtwaklGM0NkTFV4eGJ2UklVd0NnWUlLb1pJemowRUF3SXcKYURFTE1Ba0dBMVVFQmhNQ1ZWTXhGekFWQmdOVkJBZ1REazV2Y25Sb0lFTmhjbTlzYVc1aE1SUXdFZ1lEVlFRSwpFd3RJZVhCbGNteGxaR2RsY2pFUE1BMEdBMVVFQ3hNR1JtRmljbWxqTVJrd0Z3WURWUVFERXhCbVlXSnlhV010ClkyRXRjMlZ5ZG1WeU1CNFhEVEl6TURNeE9EQXlNall3TUZvWERUTTRNRE14TkRBeU1qWXdNRm93YURFTE1Ba0cKQTFVRUJoTUNWVk14RnpBVkJnTlZCQWdURGs1dmNuUm9JRU5oY205c2FXNWhNUlF3RWdZRFZRUUtFd3RJZVhCbApjbXhsWkdkbGNqRVBNQTBHQTFVRUN4TUdSbUZpY21sak1Sa3dGd1lEVlFRREV4Qm1ZV0p5YVdNdFkyRXRjMlZ5CmRtVnlNRmt3RXdZSEtvWkl6ajBDQVFZSUtvWkl6ajBEQVFjRFFnQUVQUXl3VnRnWkF0THBQd29oTEIvMDkwUDEKdmlFRmtMRFEvRkNJYXJidVVGQVovTWNlV0JKQlNkS0VPUTdBNlZSOUZsZkpZcjZCNVB5RkJya2RsWkYyRktORgpNRU13RGdZRFZSMFBBUUgvQkFRREFnRUdNQklHQTFVZEV3RUIvd1FJTUFZQkFmOENBUUV3SFFZRFZSME9CQllFCkZBdWhkZVhxeWpTVWpwaDdWRVJmdGRSWGltWlJNQW9HQ0NxR1NNNDlCQU1DQTBnQU1FVUNJUUNrMDJNZWdiUnoKQ2tCRFdia3g1UUtEcHplUitoeUJEdXRLNjdhODhpcVJaZ0lnUlZ6RXNHOEtCMy9vcEZEblA5Qk9DSEZQSEowTgo4N25EK1BkK1lOU1ZRR009Ci0tLS0tRU5EIENFUlRJRklDQVRFLS0tLS0K CAName:tls-ca IssuerPublicKey:CgJPVQoEUm9sZQoMRW5yb2xsbWVudElEChBSZXZvY2F0aW9uSGFuZGxlEkQKIPP0hMkP/e2EoHIDbRmrZJypG9o5zRFkVfZuBGSZUpTbEiCgydtTkJpTo/uu8X4cCkTqnXaqEoSXZrGhbG+2QY2nexpECiC7rjjDA8roheGkDAlTeV+5SDU1yDVia+P6yVXQyjXiexIgS2dE7l1u6Kfjma09tWZAe0TuwdxLcnS8du5PUGPn8fwiRAogNo21bukSuGl4FiNwVUXT8/5N+/T+8JDXNyKuh9ikfbgSIJdR6G4OMXzkF8gLds2QT60XLRF1RiXJ5f6IDG/41YUcIkQKICLwGYD+diqCUWtD0ONKEbvXr3R62/qNtDVVzKE2558vEiALlzfEjdAtnbybfHqPvx6fcLbxd1qTeDLi8Zn3tbKS/iJECiAI49gFcnMKEJKDGkeXtuhUMoEGK9hJWaHAvxObYiTnoRIgWQ5XPQ2EnhSlyEPLPXLuCRcGe1EsoiCELgqLhbApggIiRAogIXzXFn2NLXEaKBEYZNXj/Z01RteIpqqARJ5erJYoLYcSIHtgl1fzd7RXh7jNG1Ye+z9JRZb3LrshO5CRDrjELg5eKogBCiAjYmkBKbq2tWOUvwi6WZOz4mW4aInIFl60PCPzhXHoqhIgD1zx7CmwlRRNOI24zRFZMzDTYG92GYleShOwtmuCWcMaIDF5gLNYX4a1dwre5w0giU9bb+k4WD/lgZolY3FuFa8TIiDMC5sLCyThq2vtZJjW+uFIccuq7sgjc5PUKucYQ2TklDJECiAntdSO9QeY8uke357QSLs4Mv8A8q/mbSr9BarcZJR0CRIgD4ccwRF4J8NAzDr6cZJ+aMRK/Dq/sNdWC612WamAk/46RAogPkU57sx8P5+s9Yeei8wBQZxqRs+x8E8fbUZY7bFKEDgSIFUa7lXZCaTSOh9O0zoHrAw99uCpQe/wQVvuczXYxW/uQiDzQ/nT52EcQdB3vfG1U/1Z7YSuy8Hn5XNb11qCE0tBrUogsTmgcvmR0F5JM7cX85ysJfQMVRaF9ACGPbY+16RZKdhSIB4I31hGSuqG2vCVM9sLb27FpekfKaoO1prLt2ynCJiC IssuerRevocationPublicKey:LS0tLS1CRUdJTiBQVUJMSUMgS0VZLS0tLS0KTUhZd0VBWUhLb1pJemowQ0FRWUZLNEVFQUNJRFlnQUVuN1N4cjlzUytaWERJdjFoWUNuQjZEVGg2Z1p2RlZsNApXeFU0aVIwWDhMUHd5eCtnUjdMOXJSdytubGc1REFqMS9sdmtoWFltS1Z6NlowekdIZWlLSm5HS1lVcXlnditpCmliSXRFc1Q4Wkc0K0FJWjc2Wnh3RXM2UktYdnNiQUxSCi0tLS0tRU5EIFBVQkxJQyBLRVktLS0tLQo= Version:]]
2023/03/18 10:38:32 [DEBUG] newEnrollmentResponse rcaadmin
2023/03/18 10:38:32 [INFO] Stored client certificate at /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-client/tls-ca/rcaadmin/msp/signcerts/cert.pem
2023/03/18 10:38:32 [INFO] Stored root CA certificate at /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-client/tls-ca/rcaadmin/msp/cacerts/localhost-7054.pem
2023/03/18 10:38:32 [INFO] Stored Issuer public key at /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-client/tls-ca/rcaadmin/msp/IssuerPublicKey
2023/03/18 10:38:32 [INFO] Stored Issuer revocation public key at /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-client/tls-ca/rcaadmin/msp/IssuerRevocationPublicKey
Terminal (TLS-CA-server)
2023/03/18 10:38:32 [INFO] [::1]:50038 POST /enroll 201 0 "OK"
Step 19: Deploy an Organization-CA-server
You’ve already registered and enrolled your Organization-CA bootstrap admin rcaadmin. Besides, the signed TLS certificate is generated under fabric-ca-client/tls-ca/rcaadmin/msp/signcert and the private key is available under fabric-ca-client/tls-ca/rcaadmin/msp/keystore.
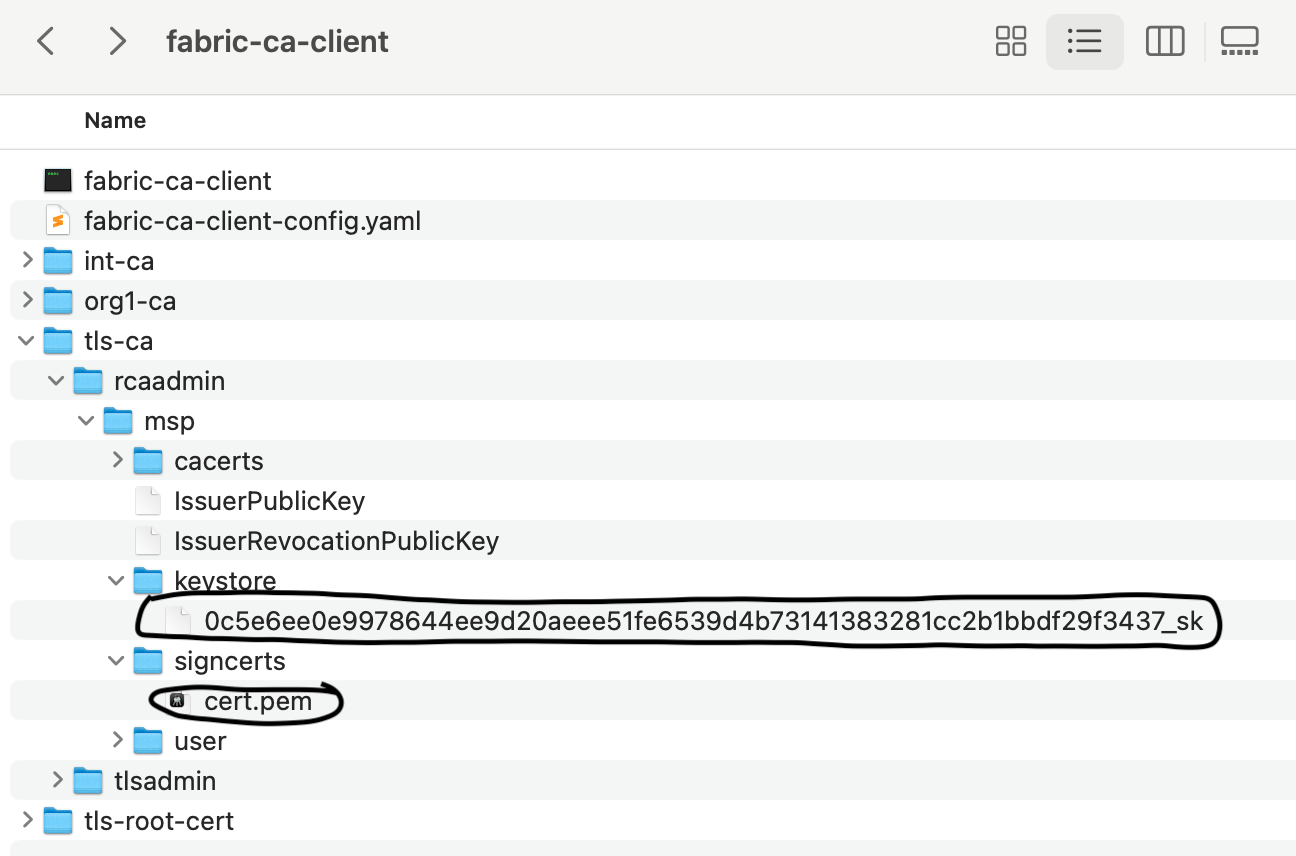
You need to copy these files under the Organization-CA directory and reference them in the tls section of the Organization-CA configuration file fabric-ca-server-config.yaml. For ease of reference, you can rename the file in the keystore folder to key.pem.
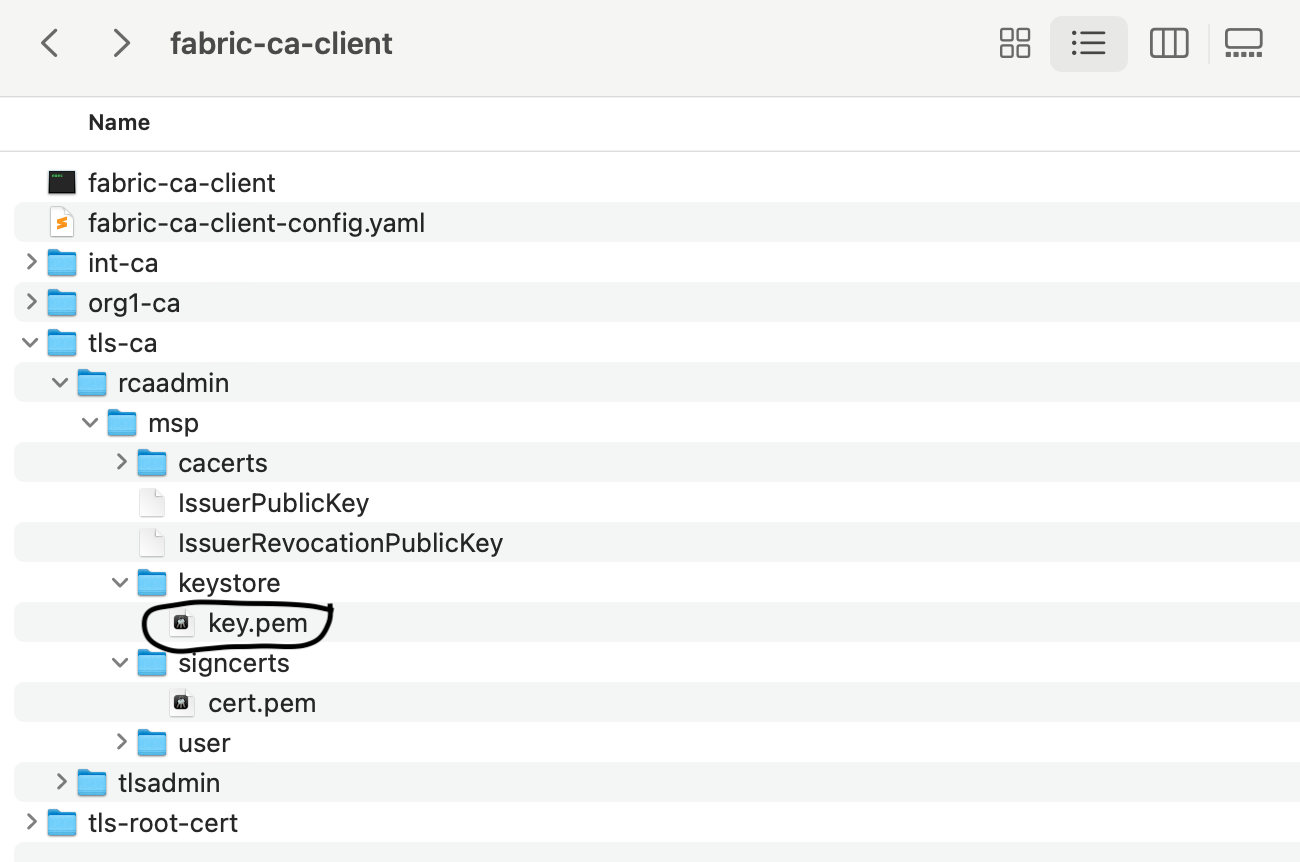
Then come up with a new directory for the Organization-CA at the root level of {Your fabric-samples repo}, you have to go up one level because you were in the fabric-ca-client directory in the previous step.
cd ..
mkdir fabric-ca-server-org1
Copy the fabric-ca-server binary and paste into this folder.
Create a folder tls for the storing of cert.pem and key.pem.
mkdir tls
Then, copy the organization Organization-CA TLS certificate and private key from the fabric-ca-client folder.
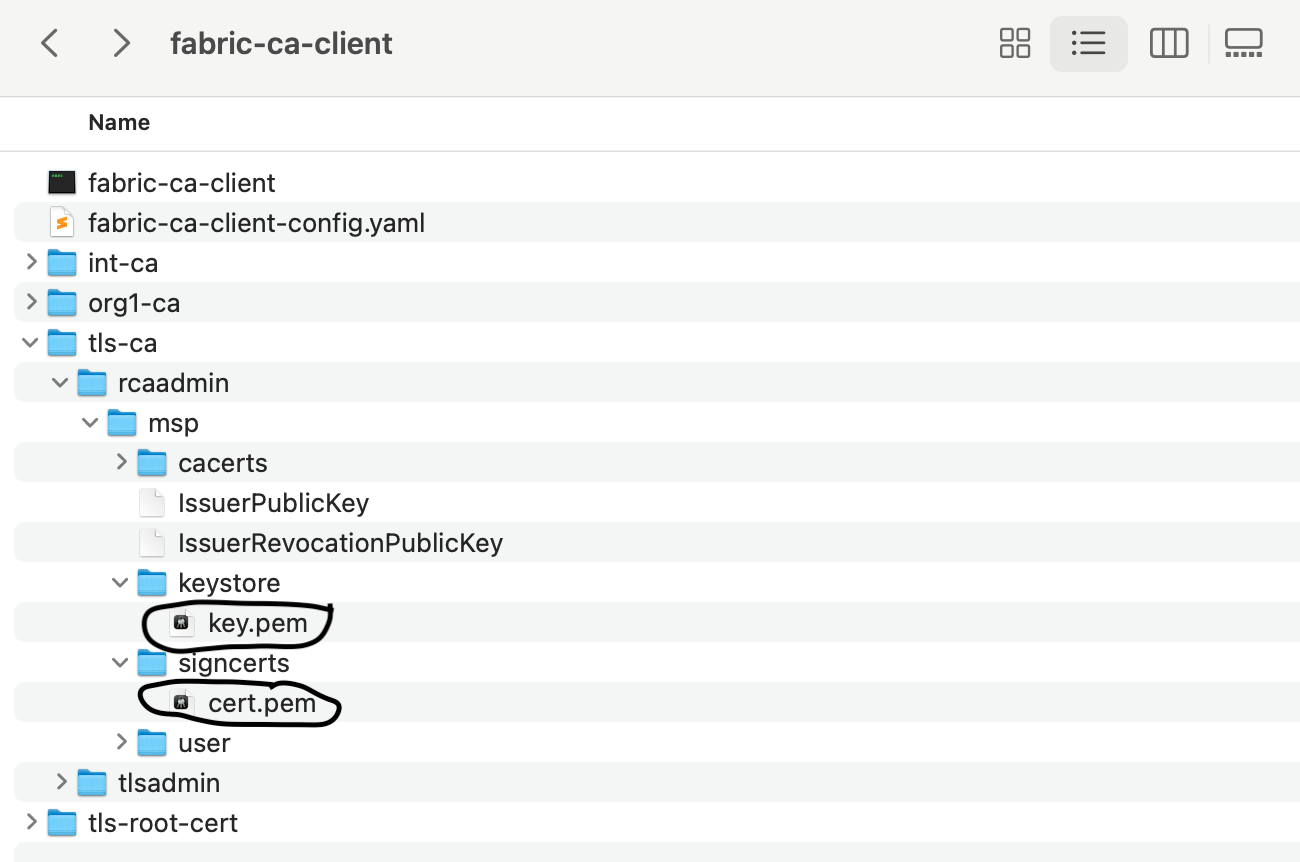
Paster them into the fabric-ca-server-org1/tls folder.
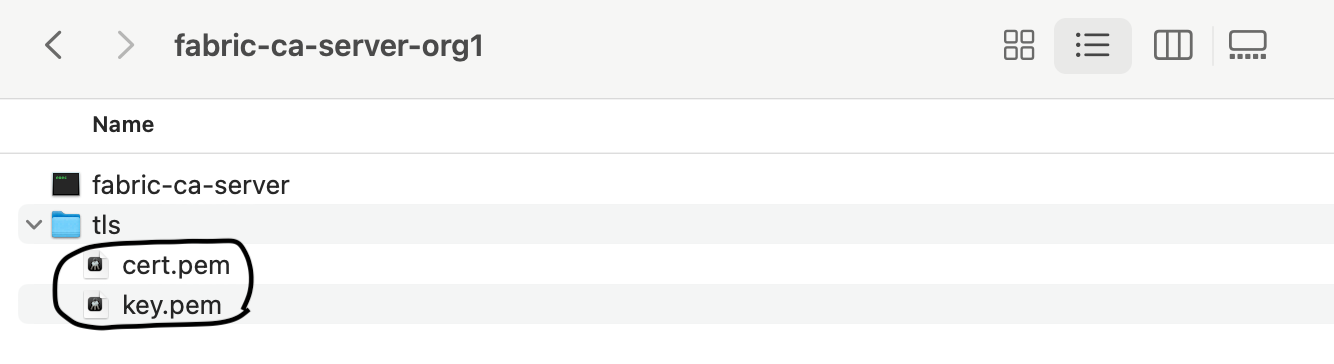
To initialize the Organization-CA-server, you have to specify an admin user id and password. Let's use the same identity rcaadmin that you registered with the TLS-CA-server before. Run the init command with the fabric-ca-server binary as such:
fabric-ca-server init -b rcaadmin:rcaadminpw
Response back: [INFO] Initialization was successful. More details:
Terminal (Organization-CA-server)
2023/03/19 11:22:03 [INFO] Created default configuration file at /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-server-org1/fabric-ca-server-config.yaml
2023/03/19 11:22:03 [INFO] Server Version: 1.5.5
2023/03/19 11:22:03 [INFO] Server Levels: &{Identity:2 Affiliation:1 Certificate:1 Credential:1 RAInfo:1 Nonce:1}
2023/03/19 11:22:03 [WARNING] &{69 The specified CA certificate file /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-server-org1/ca-cert.pem does not exist}
2023/03/19 11:22:03 [INFO] generating key: &{A:ecdsa S:256}
2023/03/19 11:22:03 [INFO] encoded CSR
2023/03/19 11:22:03 [INFO] signed certificate with serial number 170440482828155669410806920496022436235769986974
2023/03/19 11:22:03 [INFO] The CA key and certificate were generated for CA
2023/03/19 11:22:03 [INFO] The key was stored by BCCSP provider 'SW'
2023/03/19 11:22:03 [INFO] The certificate is at: /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-server-org1/ca-cert.pem
2023/03/19 11:22:04 [INFO] Initialized sqlite3 database at /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-server-org1/fabric-ca-server.db
2023/03/19 11:22:04 [INFO] The issuer key was successfully stored. The public key is at: /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-server-org1/IssuerPublicKey, secret key is at: /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-server-org1/msp/keystore/IssuerSecretKey
2023/03/19 11:22:04 [INFO] Idemix issuer revocation public and secret keys were generated for CA ''
2023/03/19 11:22:04 [INFO] The revocation key was successfully stored. The public key is at: /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-server-org1/IssuerRevocationPublicKey, private key is at: /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-server-org1/msp/keystore/IssuerRevocationPrivateKey
2023/03/19 11:22:04 [INFO] Home directory for default CA: /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-server-org1
2023/03/19 11:22:04 [INFO] Initialization was successful
Like what you've done with the TLS-CA-server just a moment ago, you need to configure the Organization-CA-server with the fabric-ca-server-config.yaml file to modify the default configuration settings for your use case. The following configurations are the bare minimum for the server to operate in a production environment.
First off, you need to determine the ports that the Organization-CA-server will use. Since the TLS-CA-server is already listening on the ports 7054 and 127.0.0.1.9443, let's use the ports 7055 and 127.0.0.1.9444 for port and operations.listenAddress instead.
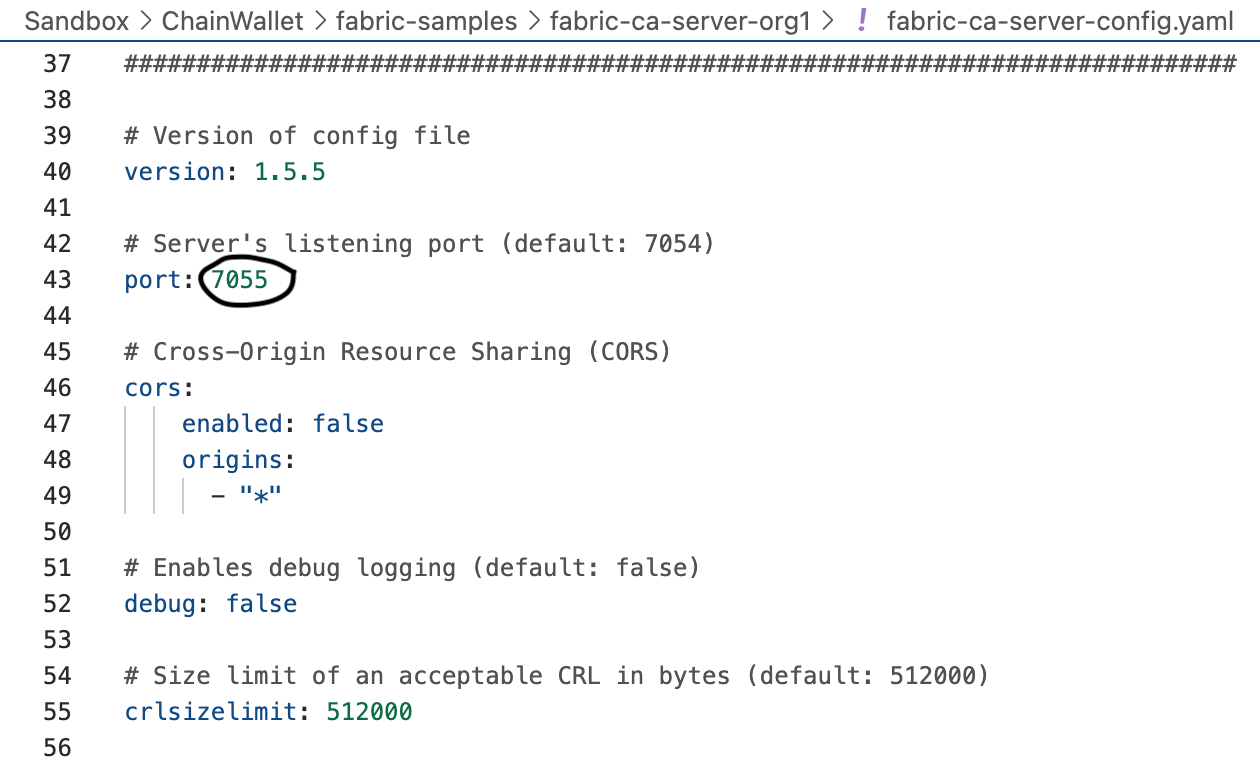
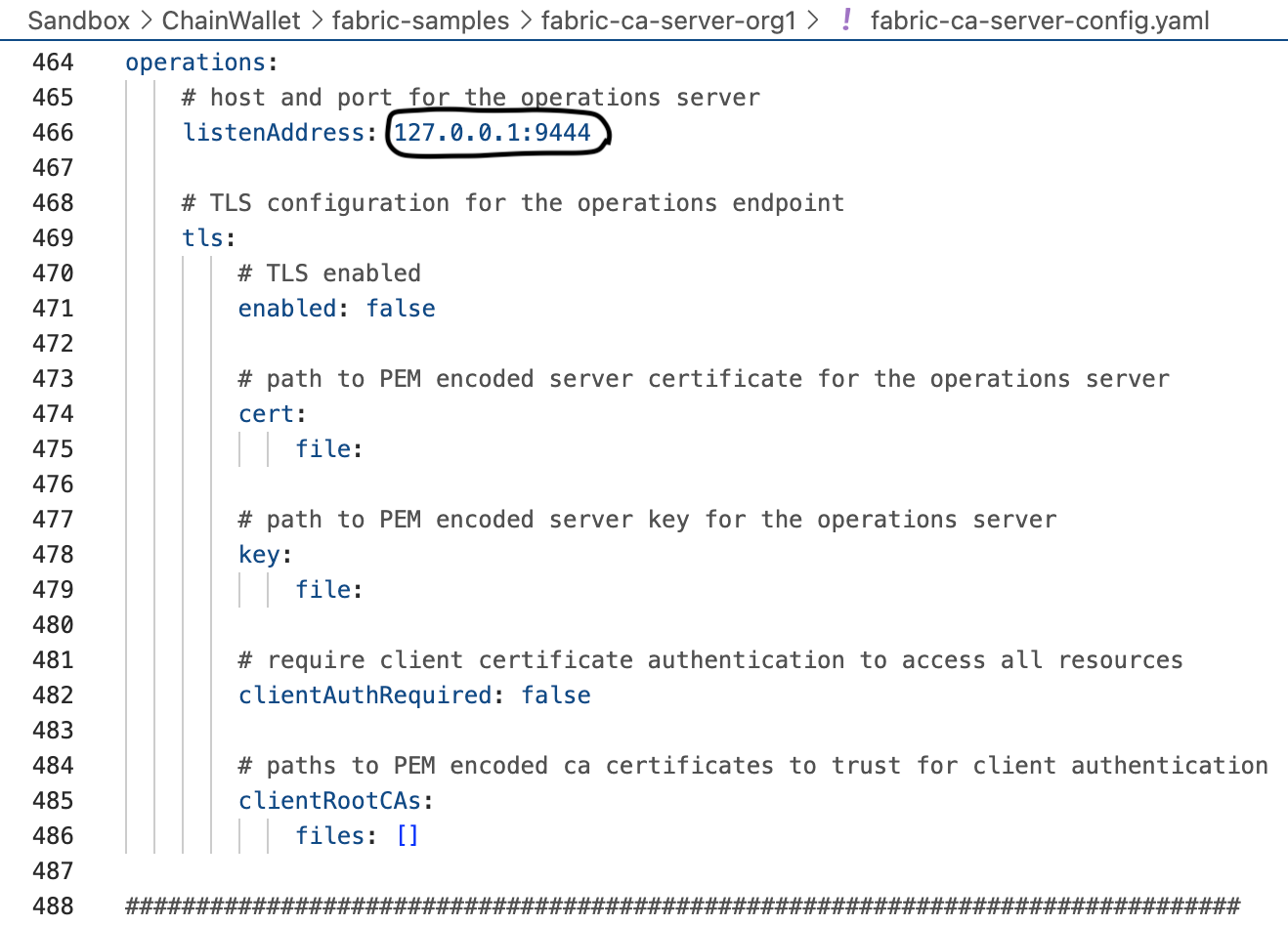
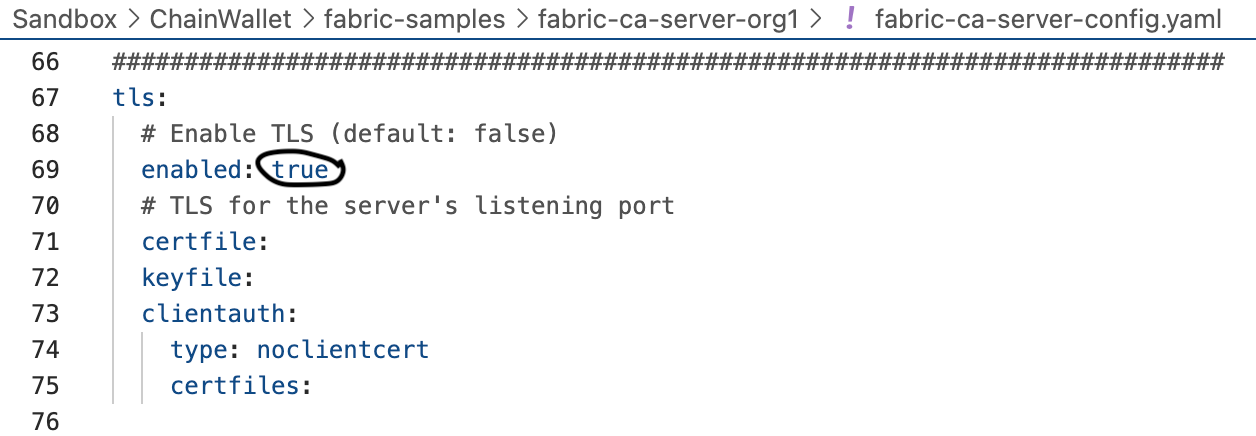
It's a production environment. TLS enabled is a must-have. Set the value to true.
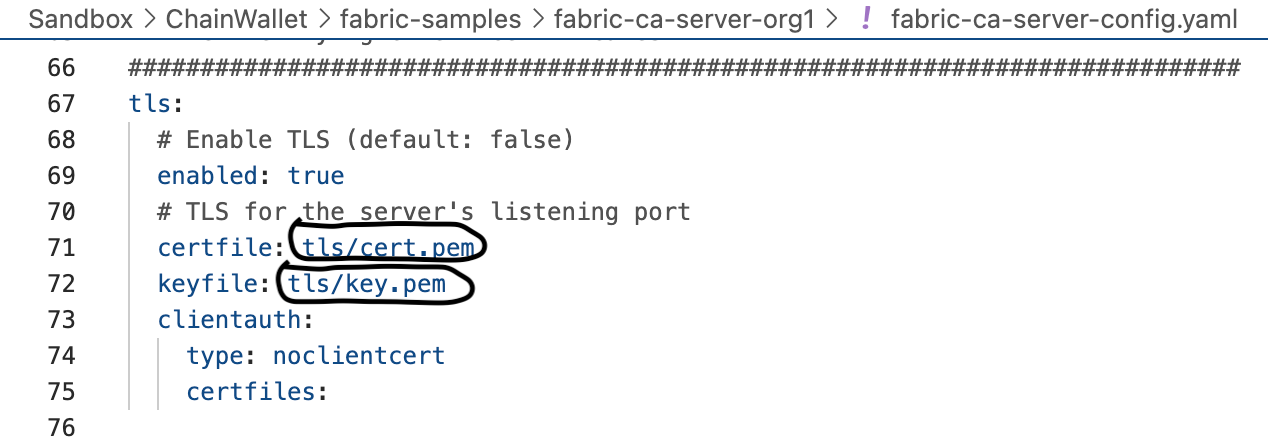
The specified path name is relative to FABRIC_CA_CLIENT_HOME you've set before. So you can simply specify tls/cert.pem for the tls.certfile and tls/key.pem for the tls.keystore.
What's the name of your Organization-CA? Let's go with org1-ca for the learning purpose.
You're set. Kick start the server now:
fabric-ca-server start
Response back: [INFO] Operation Server Listening on 127.0.0.1:9444. More details:
Terminal (Organization-CA-server)
2023/03/19 11:52:36 [INFO] Configuration file location: /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-server-org1/fabric-ca-server-config.yaml
2023/03/19 11:52:36 [INFO] Starting server in home directory: /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-server-org1
2023/03/19 11:52:36 [INFO] Server Version: 1.5.5
2023/03/19 11:52:36 [INFO] Server Levels: &{Identity:2 Affiliation:1 Certificate:1 Credential:1 RAInfo:1 Nonce:1}
2023/03/19 11:52:36 [WARNING] &{69 The specified CA certificate file /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-server-org1/ca-cert.pem does not exist}
2023/03/19 11:52:36 [INFO] generating key: &{A:ecdsa S:256}
2023/03/19 11:52:36 [INFO] encoded CSR
2023/03/19 11:52:36 [INFO] signed certificate with serial number 659008612654075303611096452721763364133191966862
2023/03/19 11:52:36 [INFO] The CA key and certificate were generated for CA org1-ca
2023/03/19 11:52:36 [INFO] The key was stored by BCCSP provider 'SW'
2023/03/19 11:52:36 [INFO] The certificate is at: /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-server-org1/ca-cert.pem
2023/03/19 11:52:36 [INFO] Initialized sqlite3 database at /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-server-org1/fabric-ca-server.db
2023/03/19 11:52:36 [INFO] The issuer key was successfully stored. The public key is at: /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-server-org1/IssuerPublicKey, secret key is at: /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-server-org1/msp/keystore/IssuerSecretKey
2023/03/19 11:52:36 [INFO] Idemix issuer revocation public and secret keys were generated for CA 'org1-ca'
2023/03/19 11:52:36 [INFO] The revocation key was successfully stored. The public key is at: /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-server-org1/IssuerRevocationPublicKey, private key is at: /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-server-org1/msp/keystore/IssuerRevocationPrivateKey
2023/03/19 11:52:36 [INFO] Home directory for default CA: /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-server-org1
2023/03/19 11:52:36 [INFO] Operation Server Listening on 127.0.0.1:9444
2023/03/19 11:52:36 [INFO] Listening on https://0.0.0.0:7055
Step 20: Enroll an Organization-CA-server bootstrap admin
The Organization-CA is used to issue identities for the organization within. You need a bootstrap admin for identity management. Run:
fabric-ca-client enroll -d -u https://rcaadmin:rcaadminpw@localhost:7055 --tls.certfiles tls-root-cert/tls-ca-cert.pem --mspdir org1-ca/rcaadmin/msp
You'll see a 201 status response back from the Organization-CA-server and a list of artifacts generated in the TLS-CA-client. More details:
Terminal (TLS-CA-client)
2023/03/19 12:11:33 [DEBUG] Set log level:
2023/03/19 12:11:33 [DEBUG] Home directory: /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-client
2023/03/19 12:11:33 [DEBUG] Client configuration settings: &{URL:https://rcaadmin:rcaadminpw@localhost:7055 MSPDir:org1-ca/rcaadmin/msp TLS:{Enabled:true CertFiles:[tls-root-cert/tls-ca-cert.pem] Client:{KeyFile: CertFile:}} Enrollment:{ Name: Secret:**** CAName: AttrReqs:[] Profile: Label: CSR:<nil> Type:x509 } CSR:{CN:tls-admin Names:[{C:US ST:North Carolina L: O:Hyperledger OU:Fabric SerialNumber:}] Hosts:[Aero-MacBookPro.local] KeyRequest:0xc0002f5ee0 CA:<nil> SerialNumber:} ID:{Name: Type:client Secret: MaxEnrollments:0 Affiliation: Attributes:[] CAName:} Revoke:{Name: Serial: AKI: Reason: CAName: GenCRL:false} CAInfo:{CAName:} CAName: CSP:0xc0000a8280 Debug:true LogLevel: Idemix:{Curve:amcl.Fp256bn}}
2023/03/19 12:11:33 [DEBUG] Entered runEnroll
2023/03/19 12:11:33 [DEBUG] Enrolling { Name:rcaadmin Secret:**** CAName: AttrReqs:[] Profile: Label: CSR:&{tls-admin [{US North Carolina Hyperledger Fabric }] [Aero-MacBookPro.local] 0xc0002f5ee0 <nil> } Type:x509 }
2023/03/19 12:11:33 [DEBUG] Initializing client with config: &{URL:https://localhost:7055 MSPDir:org1-ca/rcaadmin/msp TLS:{Enabled:true CertFiles:[tls-root-cert/tls-ca-cert.pem] Client:{KeyFile: CertFile:}} Enrollment:{ Name:rcaadmin Secret:**** CAName: AttrReqs:[] Profile: Label: CSR:&{tls-admin [{US North Carolina Hyperledger Fabric }] [Aero-MacBookPro.local] 0xc0002f5ee0 <nil> } Type:x509 } CSR:{CN:tls-admin Names:[{C:US ST:North Carolina L: O:Hyperledger OU:Fabric SerialNumber:}] Hosts:[Aero-MacBookPro.local] KeyRequest:0xc0002f5ee0 CA:<nil> SerialNumber:} ID:{Name: Type:client Secret: MaxEnrollments:0 Affiliation: Attributes:[] CAName:} Revoke:{Name: Serial: AKI: Reason: CAName: GenCRL:false} CAInfo:{CAName:} CAName: CSP:0xc0000a8280 Debug:true LogLevel: Idemix:{Curve:amcl.Fp256bn}}
2023/03/19 12:11:33 [DEBUG] Initializing BCCSP: &{ProviderName:SW SwOpts:0xc0001bd770 PluginOpts:<nil>}
2023/03/19 12:11:33 [DEBUG] Initializing BCCSP with software options &{SecLevel:256 HashFamily:SHA2 FileKeystore:0xc0001f0340 DummyKeystore:<nil> InmemKeystore:<nil>}
2023/03/19 12:11:33 [INFO] TLS Enabled
2023/03/19 12:11:33 [DEBUG] CA Files: [/Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-client/tls-root-cert/tls-ca-cert.pem]
2023/03/19 12:11:33 [DEBUG] Client Cert File:
2023/03/19 12:11:33 [DEBUG] Client Key File:
2023/03/19 12:11:33 [DEBUG] Client TLS certificate and/or key file not provided
2023/03/19 12:11:33 [DEBUG] Using curve amcl.Fp256bn for Idemix
2023/03/19 12:11:33 [DEBUG] GenCSR &{CN:tls-admin Names:[{C:US ST:North Carolina L: O:Hyperledger OU:Fabric SerialNumber:}] Hosts:[Aero-MacBookPro.local] KeyRequest:0xc0002f5ee0 CA:<nil> SerialNumber:}
2023/03/19 12:11:33 [INFO] generating key: &{A:ecdsa S:256}
2023/03/19 12:11:33 [DEBUG] generate key from request: algo=ecdsa, size=256
2023/03/19 12:11:33 [INFO] encoded CSR
2023/03/19 12:11:33 [DEBUG] Sending request
POST https://localhost:7055/enroll
{"hosts":["Aero-MacBookPro.local"],"certificate_request":"-----BEGIN CERTIFICATE REQUEST-----\nMIIBTTCB9QIBADBgMQswCQYDVQQGEwJVUzEXMBUGA1UECBMOTm9ydGggQ2Fyb2xp\nbmExFDASBgNVBAoTC0h5cGVybGVkZ2VyMQ8wDQYDVQQLEwZGYWJyaWMxETAPBgNV\nBAMTCHJjYWFkbWluMFkwEwYHKoZIzj0CAQYIKoZIzj0DAQcDQgAE+9Xw6Y5db4SL\nY/j3Sr3spS/sc1U44N4xB/gED+zR8OfPPZZqFqyDaoiKh6p0ouqajK6sV0X9jfAJ\nieyjcYbBc6AzMDEGCSqGSIb3DQEJDjEkMCIwIAYDVR0RBBkwF4IVQWVyby1NYWNC\nb29rUHJvLmxvY2FsMAoGCCqGSM49BAMCA0cAMEQCIHMrVrlIvUjkVQuIo0jhItyF\n0OMmN2WPnYSN8RadlNXMAiBx9CwYiFTDL0xbMWWN5Q0tM/oWkD1GHdrL6dwqGXRb\nqg==\n-----END CERTIFICATE REQUEST-----\n","profile":"","crl_override":"","label":"","NotBefore":"0001-01-01T00:00:00Z","NotAfter":"0001-01-01T00:00:00Z","ReturnPrecert":false,"CAName":""}
2023/03/19 12:11:33 [DEBUG] Received response
statusCode=201 (201 Created)
2023/03/19 12:11:33 [DEBUG] Response body result: map[Cert:LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUNUakNDQWZTZ0F3SUJBZ0lVYjlyaTAzNkEwTXB4bStTYTVCdmtDNHU5SXVVd0NnWUlLb1pJemowRUF3SXcKYURFTE1Ba0dBMVVFQmhNQ1ZWTXhGekFWQmdOVkJBZ1REazV2Y25Sb0lFTmhjbTlzYVc1aE1SUXdFZ1lEVlFRSwpFd3RJZVhCbGNteGxaR2RsY2pFUE1BMEdBMVVFQ3hNR1JtRmljbWxqTVJrd0Z3WURWUVFERXhCbVlXSnlhV010ClkyRXRjMlZ5ZG1WeU1CNFhEVEl6TURNeE9UQXpORGd3TUZvWERUSTBNRE14T0RBME1USXdNRm93WURFTE1Ba0cKQTFVRUJoTUNWVk14RnpBVkJnTlZCQWdURGs1dmNuUm9JRU5oY205c2FXNWhNUlF3RWdZRFZRUUtFd3RJZVhCbApjbXhsWkdkbGNqRVBNQTBHQTFVRUN4TUdZMnhwWlc1ME1SRXdEd1lEVlFRREV3aHlZMkZoWkcxcGJqQlpNQk1HCkJ5cUdTTTQ5QWdFR0NDcUdTTTQ5QXdFSEEwSUFCUHZWOE9tT1hXK0VpMlA0OTBxOTdLVXY3SE5WT09EZU1RZjQKQkEvczBmRG56ejJXYWhhc2cycUlpb2VxZEtMcW1veXVyRmRGL1kzd0NZbnNvM0dHd1hPamdZTXdnWUF3RGdZRApWUjBQQVFIL0JBUURBZ2VBTUF3R0ExVWRFd0VCL3dRQ01BQXdIUVlEVlIwT0JCWUVGSTZaaXA2bzZsYU1tQTBMCjYrK0ZXMCtDYkE3V01COEdBMVVkSXdRWU1CYUFGQUZDZEx1QnEzS0FQbUZ3SmpsY29KWS8zTTdhTUNBR0ExVWQKRVFRWk1CZUNGVUZsY204dFRXRmpRbTl2YTFCeWJ5NXNiMk5oYkRBS0JnZ3Foa2pPUFFRREFnTklBREJGQWlFQQpyZ3p1dE51RStldkZyNWNKL05IalgxWTZjMkUxSEI0b2ZKODg2bFQrOTd3Q0lGaDRmOVJVRkh0YkRNN05ESUltCnhISHZrZW0xRTdCVWhpejZLNE85MmZ4VwotLS0tLUVORCBDRVJUSUZJQ0FURS0tLS0tCg== ServerInfo:map[CAChain:LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUNGekNDQWIyZ0F3SUJBZ0lVYzI3MzNVdVZSVE5aaEtPRTNDKzRnOVJTWUk0d0NnWUlLb1pJemowRUF3SXcKYURFTE1Ba0dBMVVFQmhNQ1ZWTXhGekFWQmdOVkJBZ1REazV2Y25Sb0lFTmhjbTlzYVc1aE1SUXdFZ1lEVlFRSwpFd3RJZVhCbGNteGxaR2RsY2pFUE1BMEdBMVVFQ3hNR1JtRmljbWxqTVJrd0Z3WURWUVFERXhCbVlXSnlhV010ClkyRXRjMlZ5ZG1WeU1CNFhEVEl6TURNeE9UQXpORGd3TUZvWERUTTRNRE14TlRBek5EZ3dNRm93YURFTE1Ba0cKQTFVRUJoTUNWVk14RnpBVkJnTlZCQWdURGs1dmNuUm9JRU5oY205c2FXNWhNUlF3RWdZRFZRUUtFd3RJZVhCbApjbXhsWkdkbGNqRVBNQTBHQTFVRUN4TUdSbUZpY21sak1Sa3dGd1lEVlFRREV4Qm1ZV0p5YVdNdFkyRXRjMlZ5CmRtVnlNRmt3RXdZSEtvWkl6ajBDQVFZSUtvWkl6ajBEQVFjRFFnQUVFTzI5aStWWUxZdlV6V0lQQmw1M0pCakcKb0srajlNYk1HTUtVTE1sUXhzU3FLdlpVelRaLzF0NjExRkNzd1F2Q1NPSXJpaWRYSlFMamRWb3lOY3RHVXFORgpNRU13RGdZRFZSMFBBUUgvQkFRREFnRUdNQklHQTFVZEV3RUIvd1FJTUFZQkFmOENBUUV3SFFZRFZSME9CQllFCkZBRkNkTHVCcTNLQVBtRndKamxjb0pZLzNNN2FNQW9HQ0NxR1NNNDlCQU1DQTBnQU1FVUNJUUNqRExFV1J5TnUKMTJkMDA3V0xxbVRvMzVaaUlNeks3UVQ0cW92Nk52dWo3UUlnYXE3RTB3L2VJUGZFc1lTQlBicGJqVkJtYXpOQgpkamZMSDVtdTdnZnh4OG89Ci0tLS0tRU5EIENFUlRJRklDQVRFLS0tLS0K CAName:org1-ca IssuerPublicKey:CgJPVQoEUm9sZQoMRW5yb2xsbWVudElEChBSZXZvY2F0aW9uSGFuZGxlEkQKIGEZQwARGJvfsd3s48T0a03ldslmznoWibXSfAckGHykEiANfaf6ua983NgIVM5AnL58mAnZ2yVZLXDMdYOk+lhYmhpECiDzmOwD3t5gRz6q/5kpslsPWXzy06VFzSLLawuEWCrRRRIgi24fP43yGDtdnqvh08Sia9NLJtuM5GXhUq6j3KgMTpAiRAoggI1KWita7bYJ296fmBHUN19nojtJXc9kXeuKgDM9ARQSIGgOu5Q7eUHiKE/Uq/acD8vs7Gdk/XWeyyC5/KOwdD5eIkQKIItjtVKf7LBtKe7QqBjEQGTldft6IsKN950kUX7tk6PIEiAcOY6hY2oH8hMO+KZ+CjimbUu3HZ8z23jmBGUs10jrbSJECiAa1Yt/h1rCumxZNB9D90GnLF4GjppyCEFAEb8lqkuA6hIgi8t3DsonOWz6ltrkuEhUoC/WYDn4RU0sGEvKIe0u6ociRAogtFKjAi4GFotUiewRZIK72s2k3d6CLNhTqOy/JzHDtOcSIIcw5wcNVUHBCTEfYqD7r3FYbm1p0wVjBhHx4mwFzCHmKogBCiALTzikInHeQDsfRV0tPFSfAnp2UTJrNp3h0ASQJb3N4xIguyQ53DF9v5ekNynZOlId7Sy+p/djxzQZAoxKQW3vpCYaIA+CEKG+7KjSYLHNCAjCiACivHGAmhqZtS1mGWyNPYV2IiDZwJYzjNpqlMum0ecxn4KS+b8sH26I+AjTPFk6q7ajNjJECiALqLMns0hY4riakIWr2L17UQbAFvsbOCB9oV726fjsPRIgk+9QQulA/FWEz/JB9m17L2UpPEVr/USNcR2P+8e+Wl86RAogTYrMLwCbqUGNTPrh/YM14AKQOC7hxEISr08MN56SjCASIDphJ3DB6UsMbjwPzjkXbzTqmVfsWmlyNFSkLvF2jl0DQiBOre9LBEyLeChmYGzeWIILS8vqKJKbzZLMDPARYelYpkogY4c/g2+vaWn+xJ8l+NRPZzjUIu2FQNKwn0ovH58VJ3hSIOO0yv6AC2UWjAS1QkjYqP0wk6DR6kNmAmqKG9/m33Nx IssuerRevocationPublicKey:LS0tLS1CRUdJTiBQVUJMSUMgS0VZLS0tLS0KTUhZd0VBWUhLb1pJemowQ0FRWUZLNEVFQUNJRFlnQUVwQ1ZLdGNaUWljTHRDMkpRQ0NaS2o4T3hXQnppaVZwSQpmZVkzRDZXdU82RHhjbnkvcjJ0ODA1Z0RjMDJGUW5GMGNKb3RmVW53SndEc2NpWVNycHZpUjMrd1B3OFhxeDdzClFlN0pEQjRxbTFVczF1MFpjWGlqTjM0bVJzZXlVWnU1Ci0tLS0tRU5EIFBVQkxJQyBLRVktLS0tLQo= Version:]]
2023/03/19 12:11:33 [DEBUG] newEnrollmentResponse rcaadmin
2023/03/19 12:11:33 [INFO] Stored client certificate at /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-client/org1-ca/rcaadmin/msp/signcerts/cert.pem
2023/03/19 12:11:33 [INFO] Stored root CA certificate at /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-client/org1-ca/rcaadmin/msp/cacerts/localhost-7055.pem
2023/03/19 12:11:33 [INFO] Stored Issuer public key at /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-client/org1-ca/rcaadmin/msp/IssuerPublicKey
2023/03/19 12:11:33 [INFO] Stored Issuer revocation public key at /Users/aerobot/Documents/Sandbox/ChainWallet/fabric-samples/fabric-ca-client/org1-ca/rcaadmin/msp/IssuerRevocationPublicKey
Terminal (Organization-CA-server)
2023/03/19 12:11:33 [INFO] [::1]:49453 POST /enroll 201 0 "OK"
Step 21: Serve the End-User with Web or Mobile Application (Coming Soon)